Let us look into the latest phishing news of the week, highlighting Google’s new features, Darknet malware, crypto phishing attacks, and Russian malicious actors.
DarkGate Malware Propagated Through Phishing Attack on Microsoft Teams
A recent cyberattack has been uncovered involving a phishing campaign that exploits Microsoft Teams messages to deliver a dangerous payload known as the DarkGate Loader malware.
This nefarious campaign came to light in late August 2023, as reports emerged of malevolent Microsoft Teams phishing messages emanating from two compromised external Office 365 accounts. These accounts were compromised to deceive unsuspecting Microsoft Teams users into downloading and launching a deceptive .zip file labeled “Changes to the vacation schedule.”
Upon clicking the attachment, the .zip file containing an LNK file camouflaged as a PDF document would be downloaded from a SharePoint URL. This seemingly innocuous file harbored malicious VBScript code that catalyzed the infection process, ultimately leading to the deployment of the DarkGate Loader.
As found by researchers at Truesec, the phishing campaign leveraged compromised Microsoft Teams accounts to disseminate malicious attachments to other organizations that used Teams. The approach bore similarities to a June 2023 report by Jumpsec, which demonstrated the exploitation of Microsoft Teams for malicious messaging, using phishing and social engineering tactics.
While DarkGate may not yet pose a widespread threat, its expanding range of targets and adoption of diverse infection avenues necessitates vigilant monitoring as it emerges as a potential cyber threat on the horizon.
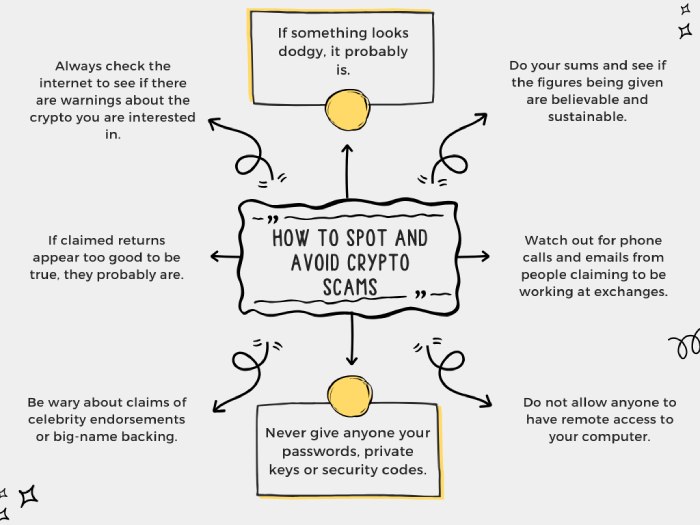
Phishing Scam Steals $24 Million from Ethereum Wallet in Major Crypto Theft
A phishing attack targeted an Ethereum address known for its interactions with DeFi (Decentralized Finance) protocols, resulting in substantial losses exceeding $24 million in cryptocurrencies.
The attacker executed the theft by deceiving the victim into visiting a malicious website and authorizing “Increase Allowance” transactions on their digital wallet. The stolen assets comprise approximately $8.5 million worth of Rocket Pool ETH (rETH) and around $15.6 million in Lido Staked ETH (stETH). Both rETH and stETH are Ethereum-based derivatives designed for users to stake their ETH and receive rewards.
Scam Sniffer, a blockchain security enterprise, uncovered the exploit and confirmed that the threat actor had initiated transfers of the stolen funds. A portion of the funds was moved to FixedFloat, an instant cryptocurrency exchange supporting the Bitcoin Lightning Network. A significant share of the stolen assets is currently held in three separate, unrelated addresses.
Notably, the attacker’s address has connections to numerous cryptocurrency phishing websites. The victim’s identity remains undisclosed, but on-chain data indicates that the targeted address was actively involved in the DeFi ecosystem. It had contributed liquidity totaling $1.6 million on Uniswap V3 and had utilized various DeFi platforms, including Aave, Curve, and 1inch.
This incident is a reminder of the persistent and evolving threat posed by sophisticated phishing schemes within the cryptocurrency sector. The incident came shortly after Kroll, the claims agent involved in FTX’s bankruptcy proceedings, experienced a cybersecurity breach, compromising customer data belonging to claimants in the ongoing bankruptcy case.
US Authorities Bring Charges Against 9 Russians Linked to Cyberattacks on American Organizations
Earlier this week, the DOJ (Department of Justice) unveiled charges against nine Russian nationals, accusing them of utilizing Russian-based malware in cyberattacks aimed at siphoning funds from various US entities, including corporations, government agencies, and educational institutions.
The individuals named in the charges are Mikhail Tsarev, Maksim Galochkin, Andrey Zhuykov, Sergey Loguntsov, Dimitry Putlin, Max Mikhaylov, Valentin Karyagin, Makism Rudensky, and Maskim Khaliullin. According to the DOJ, they allegedly harnessed malicious software tools, specifically Trickbot and Conti, to infiltrate the devices of American victims.
Attorney General Merrick Garland stated that the perpetrators are linked to a ransomware variant widely used in the United States. Their activities encompassed attacks on various targets, including local police departments and emergency medical services.
One of the indictments details how the accused infected victims’ computers with Trickbot malware. It was designed to harvest sensitive personal data such as banking credentials, passwords, and personal identification information, including credit card and email data.
Subsequently, the threat actors leveraged these stolen login credentials to drain funds from victims’ bank accounts. To compound the damage, they also deployed ransomware on the compromised computers. The accused are believed to reside in Russia and do not have legal representation in the US.
National Security Council’s former senior director for counterterrorism, Javed Ali, opined that these individuals will unlikely face justice. However, he noted that the DOJ’s recent indictments underscore the United States’ commitment to holding malicious actors accountable for their actions.
Google Chrome’s Real-Time Phishing Protection Now Available to All Users
Google has unveiled a significant enhancement to its web browser, Google Chrome, to bolster user security. Google announced today that it will introduce real-time phishing protection to the existing standard Safe Browsing feature, extending this security measure to all users.
Recognizing the latest need to bridge the gap between threat identification and prevention, Google is now extending real-time protection to the standard Safe Browsing feature. Earlier, the locally hosted Safe Browsing list was only updated every 30 to 60 minutes, whereas 60% of phishing domains remain active for just 10 minutes.
By upgrading Safe Browsing to check sites in real-time against Google’s known malicious sites, Google anticipates a 25% improvement in protection against malware and phishing threats.
Google is implementing the real-time protection feature in a more privacy-preserving manner through Fastly Oblivious HTTP Relays. This protocol conveys users’ partially hashed URLs to Google’s Safe Browsing engine without exposing private information such as IP addresses and request headers. However, this approach has a limitation: it cannot heuristically determine if a URL is malicious without first being flagged by Google.
However, if the user is ready to compromise on some privacy, they can turn on Enhanced Protection mode, which offers even higher security with the help of AI. Google has reassured users that the real-time protection feature will not be employed for delivering advertisements.

![Teams Phishing Spreads Malware, Crypto Theft Heist, Russian Cyberattack Charges – Cybersecurity News [September 04, 2023]](https://www.phishprotection.com/wp-content/uploads/2023/09/phishing-prevention-1.jpg)