Advanced Threat Defense
Six Email Protection Technologies in One
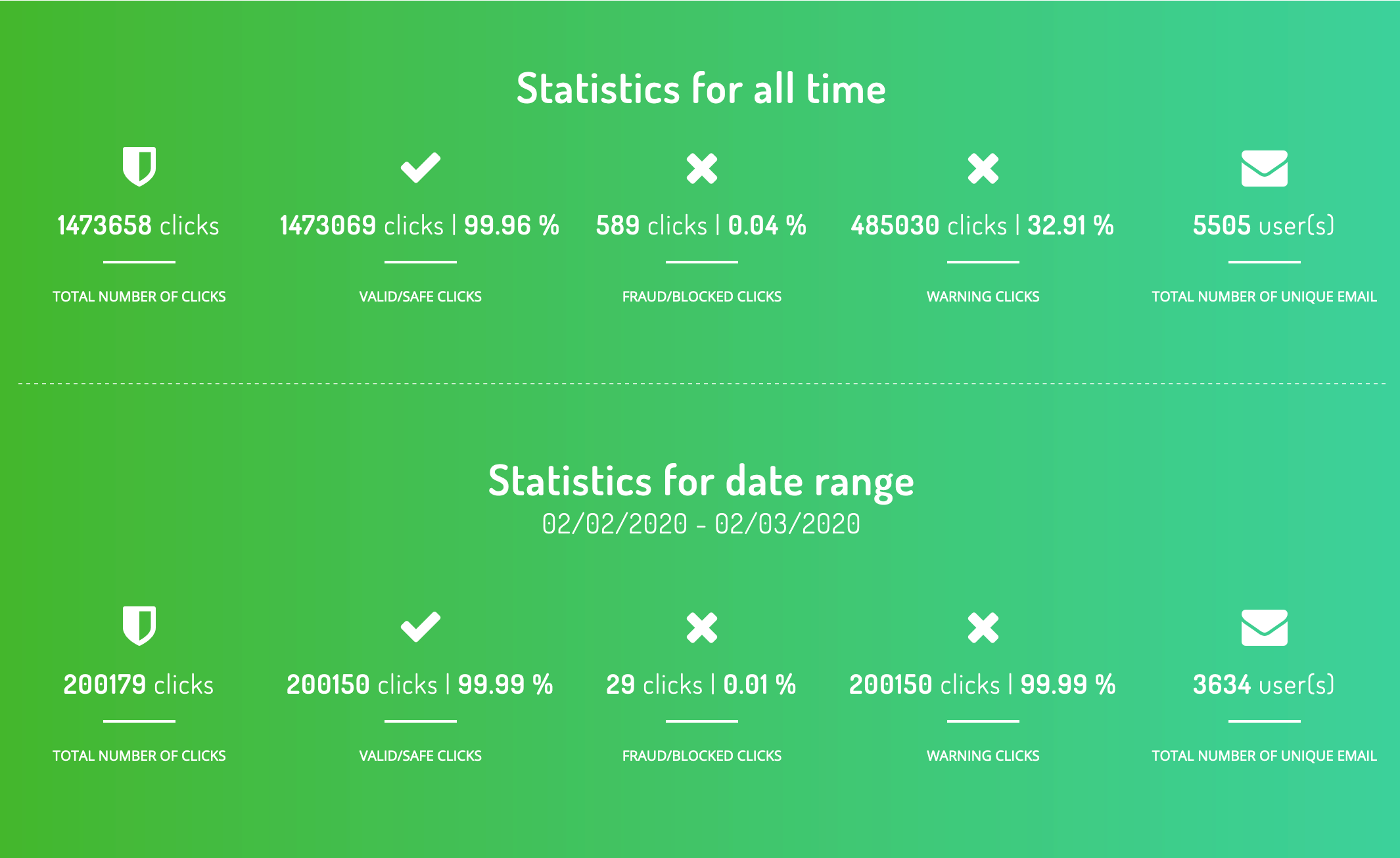
PhishProtection, which includes Advanced Threat Defense, is a cloud-based, integrated, email protection suite of services that stops phishing, malware, spam and spoofing.
Real-Time Link Click Protection
Most anti phishing solutions check emails for malicious links before they hit your inbox. But today, that’s just not good enough. Because attackers can send seemingly safe emails that later turn malicious, links in emails must be checked in real-time.
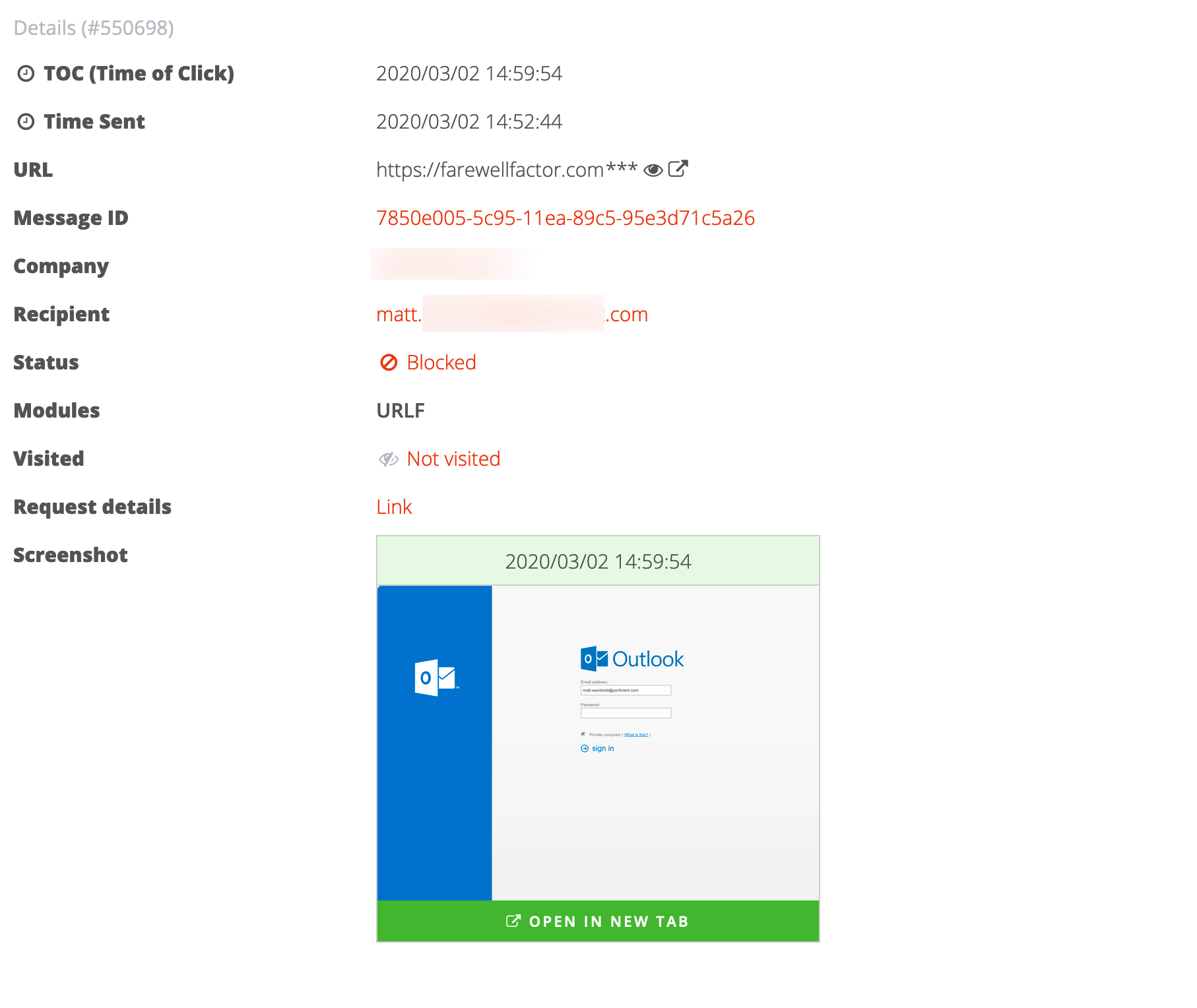
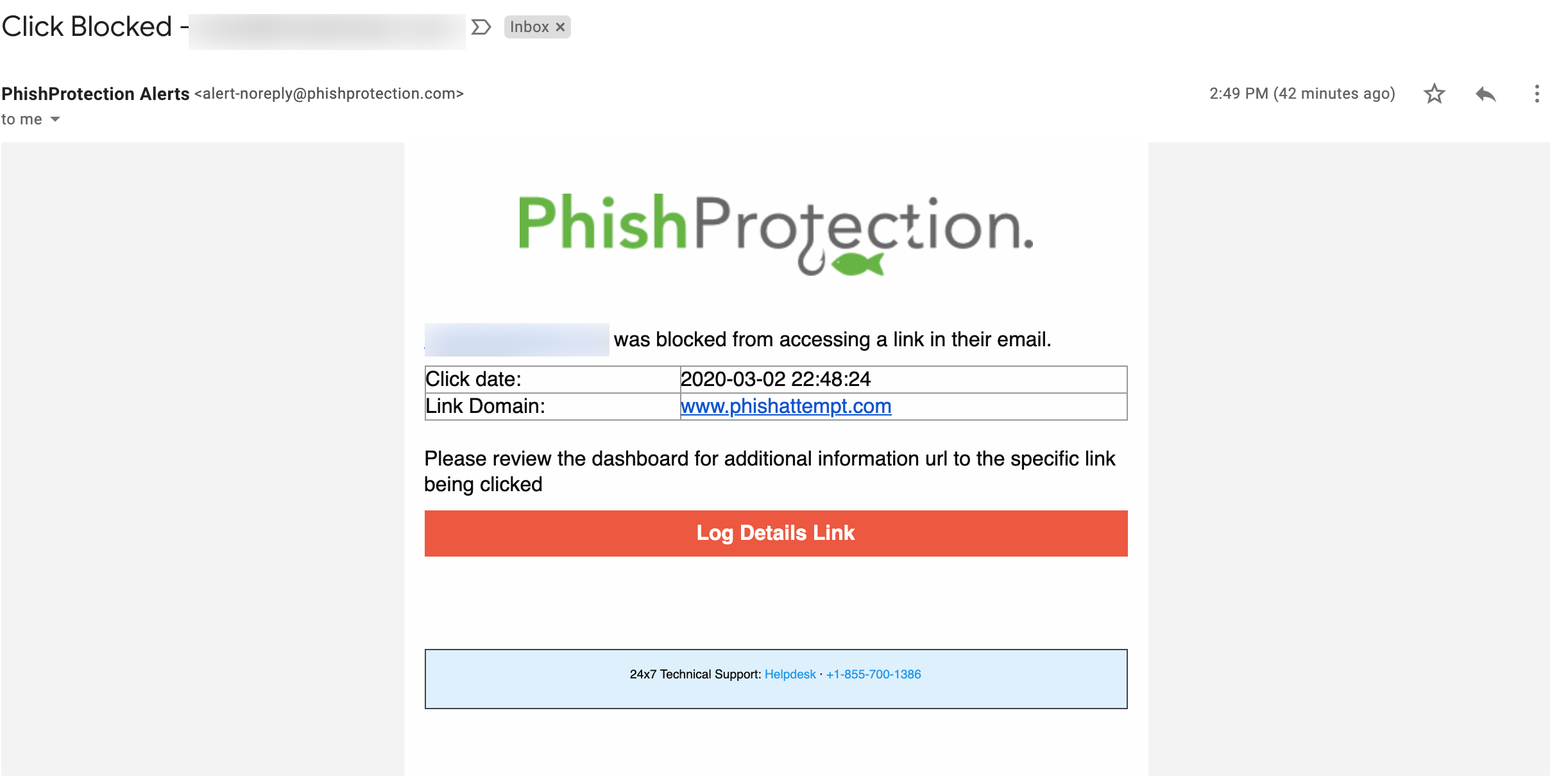
Advanced Threat Defense checks links in emails when they’re clicked. Every time they’re clicked. So, you’re protected from time-delayed phishing techniques—one of the most sophisticated approaches employed by attackers today. With it you get total phishing prevention.


Smart Quarantine
Did you ever miss an expected email only to discover later that it got stuck in your spam folder? That’s called a false positive and it happens because even the best spam filters aren’t perfect. Wouldn’t it be nice if you never had to look in your spam folder again?
Advanced Threat Defense uses Smart Quarantine to all but eliminate false positives for emails misclassified as spam. By notifying the sender that their message was quarantined and giving them the opportunity to release the message to you themselves, emails intended for you get to you without your intervention. The system learns and adjusts so it happens less frequently as time goes by.
Domain Name Spoofing Protection
It’s possible to register internationalized domain names (IDN) with foreign characters that look just like ASCII characters. For example, the Cyrillic “а” is different than the ASCII “a” even though they look identical. That makes it difficult for users to distinguish a spoofed IDN domain from a legitimate one.
Advanced Threat Defense mitigates the threat of domain name spoofing by creating a customized list of IDNs for the domains you own and then adding them to the blocked list. This helps to automatically block cybercriminals attempting to spoof internal emails, which is the greatest threat against executives at your company, giving them spear phishing protection.

Display Name Spoofing Protection
Email clients exacerbate the phishing problem by only displaying the name, and not the full email address of, the sender. Sophisticated attacks take advantage of this by falsely displaying the name of top executives. This can be used to deceive employees into disclosing sensitive information or executing unauthorised transactions.
Advanced Threat Defense helps prevent display name spoofing by alerting recipients when a display name in an email is similar to the display name of an executive. This helps to protect your company against being defrauded.
Malicious Attachment Blocking
There’s no reason for anyone at your company to ever receive an email with an executable file attached, which is why Advanced Threat Defense blocks them all. So, you never have to worry about someone accidentally double clicking one.
Advanced Threat Defense also scans non-executable files for embedded macros and scripts, as well zips files up to nine levels deep. Blocked attachments are quarantined and the sender is notified the attachment has been blocked.


Real-Time Access to Mail Queue and Activity Log
Just because you engage a third party service provider to protect your employees from phishing attacks, doesn’t mean you want to be in the dark about what’s going on. You want your IT administrators to have real-time access into what email is coming in and what’s been done with the emails that have already arrived.
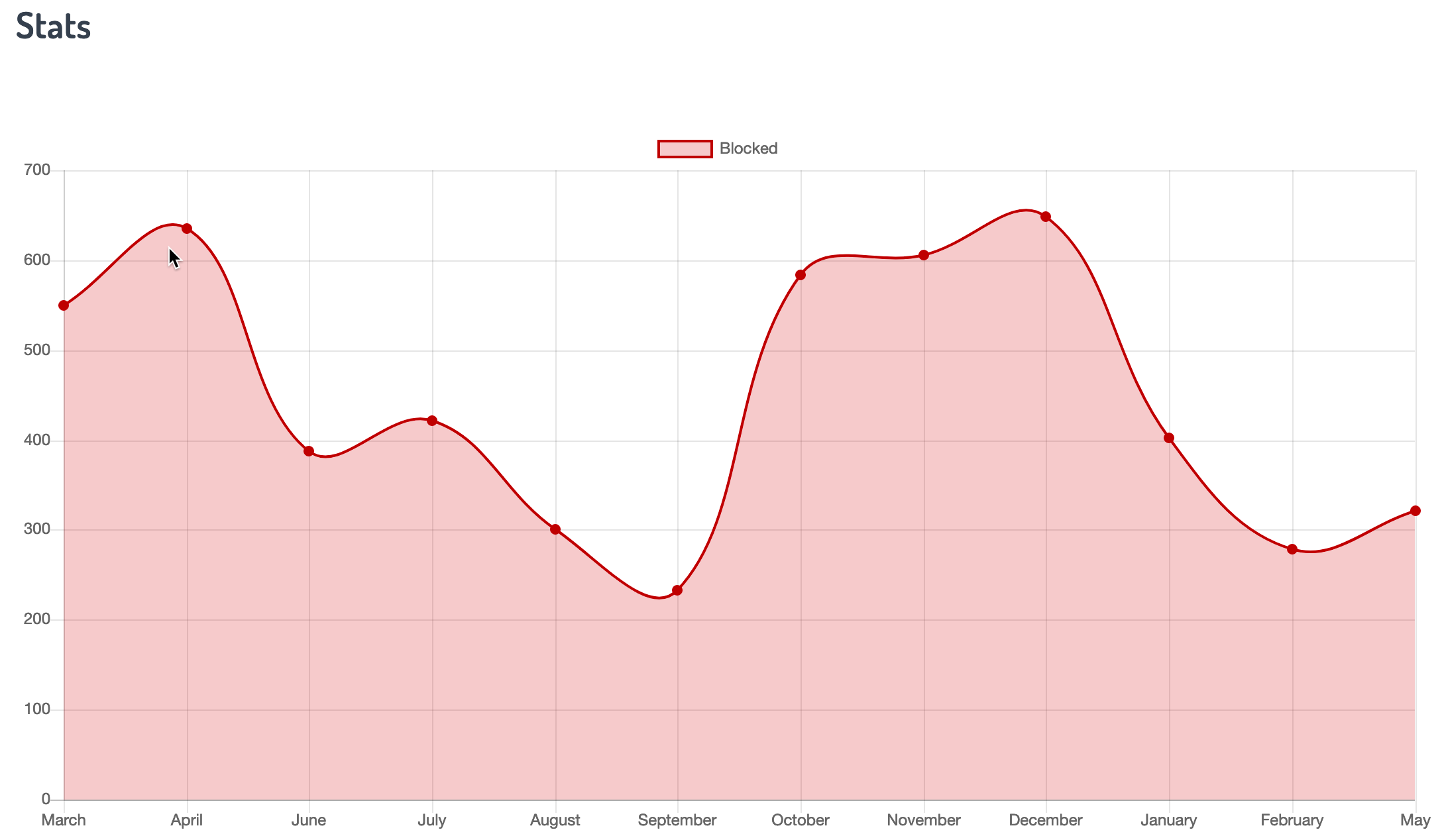
Advanced Threat Defense offers you complete situational awareness of your system from a single unified web-based console. It include real-time access to the activity log and email queue. The console also enables you to control your protection. You have the ability to fine tune your filters and customize your whitelists and blacklists.
Realtime Protection Against Phishing, Ransomware & Email Fraud
Getting Advanced Threat Defense is Fast, Easy and Affordable
Works for All Systems and All Devices
Whether you’re using Mac, Windows, iOS, Android or Linux – we’ve got you covered. If you run a hosted system like Office 365, try our office 365 advanced threat protection solution.
- No sales calls
- No contracts
- Up and running in ten minutes
Multiple layers of anti-virus, impersonation and phishing protection
OUTBREAK PROTECTION
Cyren protects your email from internet threats by analyzing over 16 billion transactions per day and protecting over 550 million users in 190 countries.
TOP RATED ANTIVIRUS
Sophos takes security far beyond traditional antivirus. It delivers advanced, real-time protection from the latest ransomware, malicious software, and hacking techniques.
REAL TIME DATABASE
PhishTank provides us with the latest data on cyberattack technologies and techniques found in the wild. This lets us protect users from new vulnerabilities in real-time.
GOOGLE PROTECTION
Google protects over three billion devices every day by showing warnings to users when they attempt to navigate to dangerous sites or download dangerous files. We use their webrisk API to classify URLS.
VADE SECURE
Email security to give you email-borne phishing protection, phishing and malware protection, malware, and ransomware. Email security and management.
INTERNET SECURITY
Cloud-based protection that stops threats in real time and secures businesses and individuals wherever they connect. Provides time of click protection and highly refined URL classifications.