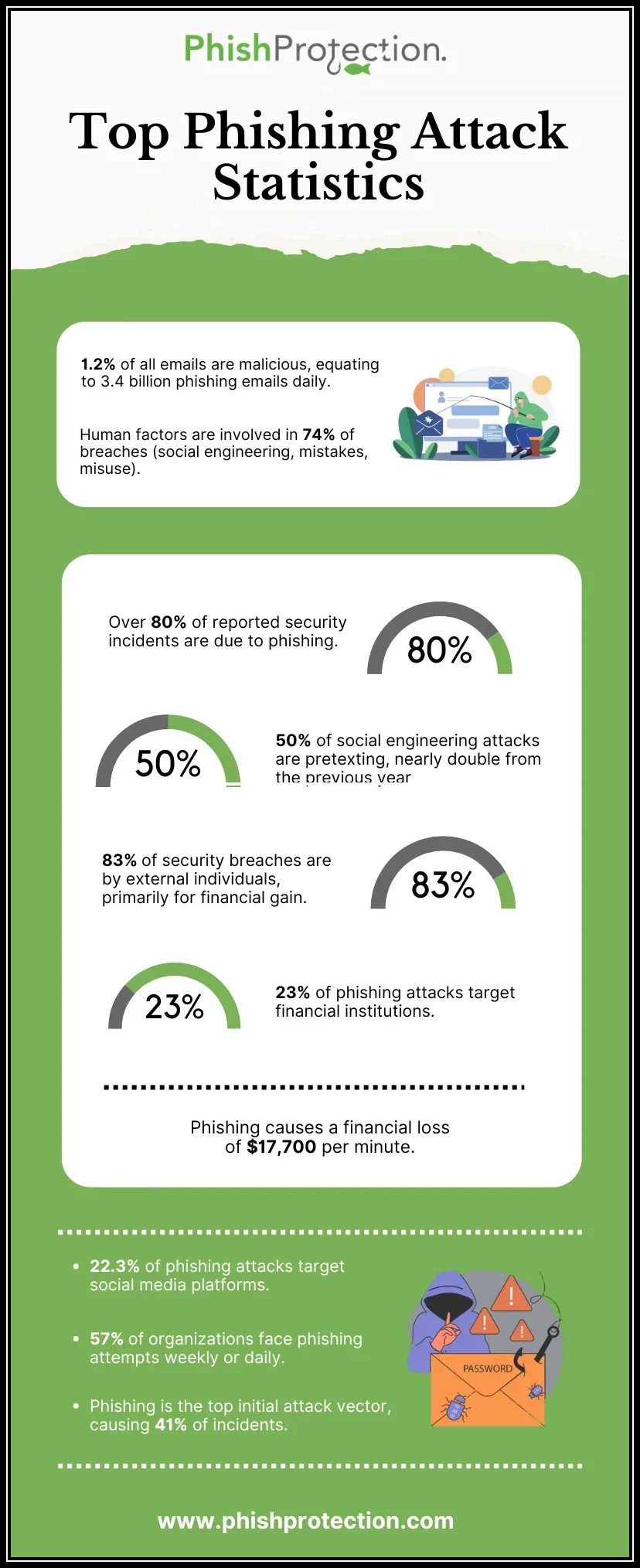
Even though businesses are bracing up for cyberattacks by embracing advanced security measures, threat actors somehow manage to stay ahead of the race by adopting smart, malicious tactics.
Big and small businesses, especially those in the financial sector, followed by social media and SaaS, are the worst hit by phishing emails. Microsoft, the tech giant itself, blocks as many as 15 billion suspicious emails on a daily basis!
That’s precisely why, the need of the hour is to stay well-versed with the latest technical advancements and security measures to secure sensitive business data.
This article aims at walking you through the pre-requisites of safeguarding your business data from the prying eyes of threat actors.
Understanding Phishing Attacks Closely
A phishing attack is a type of cyber attack that threat actors leverage to break into your bank. They do so by impersonating big brands and sending out malicious emails, text messages or telephone calls. The ultimate goal is to steal sensitive business details by tricking naive users into clicking suspicious links.
Extent of Damage Caused By Phishing Attacks!
Phishing attacks can do a lot of damage to your business. Here’s how:
- It can result in operational disruption.
- It may lead to severe data breaches.
- It can harm your brand reputation and spoil goodwill.
- It can result in permanent loss of important data.
- It can empty your bank account.
- It may even lead to regulatory penalties.
Major Types Of Phishing Attacks Your Business May Come Across!
Email bombing
All of a sudden, your business inbox will get flooded with endless spammy emails sent by threat actors. The idea is to confuse you and divert your attention from priority emails. In this confusion, you may end up clicking on any link, which may further download any malware into your system.
Clone phishing
The threat actor will replicate legitimate email content as closely as possible and then replace the original link with a malicious one. If you get fooled by the cloned email content, you will click on the fake link by mistake and BOOM- you may lose all your data in a matter of seconds.
Spear phishing
It is more like sending personalized cold emails. Threat actors send out personalized cold emails to deceive a specific brand or person.
MITM
Also known as the Man In The Middle, this phishing type involves a threat actor who intercepts a communication thread between two individuals. They remain unaware of the third party’s involvement and can continue with their top-secret business communications.
Whaling
This is like targeting the leader of the pack! Threat actors target the decision-makers in an organization with significant hold, influence and access to important matters.
BEC
Also termed as Business Email Compromise, the attackers aim at targeting businesses that deal in foreign supplies and involve transfer payments as a part of their daily business.
Common Phishing Tactics Used Against Business Organizations
Website spoofing
Threat actors come up with an illegitimate domain that looks similar to the original one.
Email spoofing
In this case, threat actors send out spammy emails through a fake sender address.
Link manipulation
Threat actors often create fake links by interchanging the alphabet or misspelling a specific word. A naive user, when in a hurry, will click on this fake link and fall prey to a phishing attack.
Image phishing
In this case, malicious codes are embedded in image files, which in turn take you to a phishing website.
Popup windows
This tactic is used by threat actors to trick users into downloading malicious software by accidentally clicking on a pop-up window.
3 Tell-Tale Signs To Identify A Phishing Email
Here are a few tell-tale signs of a phishing email:
- Mismatched subject and content of the email.
- Grammatical mistakes, poor spelling errors and urgent requests in the email content.
- Suspicious file extensions (.js, .exe, .docm, .scr, .zip)
3 Tips to Safeguard Your Business From Imminent Phishing Attacks!
Adopting fool-proof security policies.
Chart out stringent anti-phishing policies that highlight the roles and responsibilities of employees and team members in case they receive any suspicious emails. The policy should also emphasize the legitimate use of company devices, password accessibility, data handling, and so on.
Advanced training across all the departments.
Train your employees about password security, filtering emails, reporting suspicious emails, and safely sharing files by using a word to PDF converter to transform editable documents into secure PDFs with Canva’s features. Keep organizing phishing awareness training from time to time.
Embracing technical defences.
Invest in high-end anti-phishing software that offers all-encompassing security to your organization against threat actors.
Remember that prevention is better than cure. Having a proven anti-phishing system in place ensures minimal ramifications and enables the organization to act swiftly. Also, keeping your calm and deciding the next moves strategically after a phishing attack actually helps!
So, stay vigilant and work on developing a secure phishing protection system for your business organization.