With discoveries of Chinese malicious actors and new APT groups, our Weekly Cybersecurity Bulletin brings you the top cybersecurity news from around the globe. These underscore the importance of implementing cutting-edge phishing protection solutions.
US Critical Infrastructure Breached by Chinese Adversaries in Covert Attacks
Volt Typhoon, an active cyber espionage group from China, has been relentlessly targeting organizations based in the United States since mid-2021.
Their operations target critical sectors, including communications, manufacturing, transportation, construction, utilities, and education. The esteemed Threat Intelligence Team at Microsoft discovered these malicious activities.
It determined that the threat actors behind Volt Typhoon leveraged zero-day vulnerabilities to exploit Internet-exposed Fortinet FortiGuard devices, breaching their security defenses. The group adeptly utilizes widely available open-source tools like Impacket and Fast Reverse Proxy (FRP) to carry out their sophisticated attacks.
They also exploit SOHO (Small Office and Home Office) network equipment vulnerabilities, effectively stealing credentials that enable them to deploy web shells for data extraction.
Recognizing the severity of the situation, Microsoft has taken swift action by proactively reaching out to all affected customers, offering comprehensive support and vital information to fortify their network defenses against future attacks.
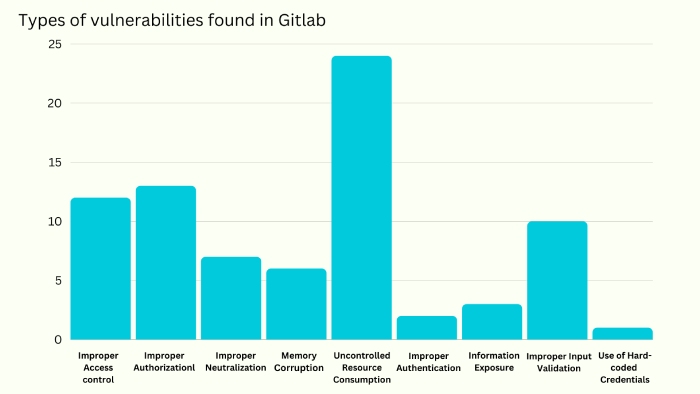
Urgent Patching Required for Maximum Severity Flaw, GitLab Advises
GitLab released a new emergency security update that users need to install promptly. Security release version 16.0.1 by GitLab addresses CVE-2023-2825, a path traversal flaw with a CVSS score 10.
Discovered and reported by “pwnie,” the vulnerability arises from a path traversal, exploiting which a threat actor can read arbitrary files on the server whenever a public project nested attachment exists in five or more groups. It could expose confidential information such as software code, credentials, files, tokens, etc.
GitLab released a security advisory that strongly recommended all individuals upgrade to the latest version to protect against this menace.
WordPress Sites of 1.5 Million Users Targeted by Malicious Actors Exploiting Cookie Consent Plugin
A significant attack vector has started making rounds targeting a specific vulnerability called Unauthenticated XSS (Stored Cross-Site Scripting). It works through the Beautiful Cookie Consent Banner, a widely used WordPress cookie consent plugin.
The vulnerability affects over 40,000 active installations, with malicious actors injecting JavaScript code into vulnerable websites, potentially leading to unauthorized access, session hijacking, malware infections, or complete system compromise.
Security enterprise Defiant discovered the attacks, which exploit the vulnerability to create rogue admin accounts on WordPress websites running outdated plugin versions. The flaw was patched in January with the release of version 2.10.2. While the current attacks may not deliver a payload, website owners should update the plugin to prevent the corruption of its configuration.
Threat actors also attempt to exploit other WordPress plugins’ vulnerabilities, such as Essential Addons for WordPress Advanced Custom Fields.
Israeli Organizations Targeted by Iranian Threat Actors Utilizing New Moneybird Ransomware
Agrius, an Iranian state-sponsored threat actor group, is behind a novel “Moneybird” ransomware that targets Israeli enterprises.
The group is responsible for attacks against organizations in the Middle East, especially Israel, and has employed multiple aliases, deploying data wipers since 2021. The researchers at CheckPoint discovered a new strain of ransomware that Agrius has developed to expand operations.
The threat actors gain access to organizational networks by exploiting public server vulnerabilities and hiding behind Proton VPN. Agrius deploys web shells, exfiltrates victim data, and downloads Moneybird ransomware from file hosting platforms that execute and encrypt all target files.
Moneybird is a simple but effective ransomware model that can disrupt business operations as of now, and it may become an even more significant threat once advanced versions are developed.
Zero-Day Flaw Exposes Email Gateways to Breach, Barracuda Issues Warning
Email and network security solutions giant Barracuda warned its customers that ESGs (Email Security Gateways) are getting breached due to a new zero-day fault.
Barracuda discovered a vulnerability in the email attachment scanning module on May 19, which was patched. However, even after the patch was released, Barracuda issued a security alert highlighting that ESG appliances were compromised with the newly patched bug.
The organization also sends notifications to customers using the ESG user interface on the actions and clarifies that other products are unaffected by this zero-day vulnerability.
Barracuda said the investigation spanned only the ESG product, not corporate networks. Therefore, impacted organizations should review and confirm any presence or spread of a threat actor.
Silent Government Attacks Traced Back to GoldenJackal State Malicious Actors
A previously unknown APT (Advanced Persistent Threat) actor group has been targeting Asian governments and diplomatic organizations in espionage attacks since 2019.
Called the “Golden Jackal,” the threat actors maintain a low profile adopting a stealthy approach and choosing targets carefully to reduce exposure. Kaspersky’s researchers reported that the APT group activity was noticed in Afghanistan, Iran, Iraq, Turkey, and Pakistan.
The threat actor group employs custom .NET malware tools to steal data, load malware, perform lateral movement, and exfiltrate files. JackalControl malware is primarily used, which is run as a program to establish a presence and receive commands from a C2 (Command and Control) server for all kinds of malicious activities.
Little is known about the Golden Jackal, but the diversity of its toolkits and the infectious chain of attacks highlight how severe the group is.