[sonaar_audioplayer albums=”243016, 243069, 243091, 243115, 243151, 243173, 243195, 243238, 243291, 243308, 243324, 243335″ progress_bar_style=”default” wave_bar_width=”1″ wave_bar_gap=”1″ player_layout=”skin_boxed_tracklist” show_track_market=”true”][/sonaar_audioplayer]
Fortinet, a security vendor based in California, has recently released an official confirmation regarding a data breach. The hacker, known by the name of FortiBitch, has leaked 440GB worth of data on BreachForums. Fortinet believes that the data breach is not that big of a deal and has impacted only a ‘small number’ of Fortinet users.
Fortibitch managed to access the data from the Azure Sharepoint site and then demanded a ransom from Fortinet. However, as the latter refused to pay the ransom, the hacker went on and leaked the data online. This cyberattack hints at the staggering risk companies put their customers through by ignoring appropriate security measures while using third-party cloud repositories.
As of now, Fortinet is unable to identify the exact source of a data breach. However, the security company released an advisory for its customers stating that some hacker had managed to gain ‘unauthorized access to a limited number of files stored on Fortinet’s instance of a third-party, cloud-based shared file drive.’
Fortinet believes that a mere 0.3% of its customer base, i.e., 2325 users, have been affected by the unforeseen instance of data breach. The company also said that so far, no malicious activity has been carried out by leveraging the leaked data.
As soon as they learned about the data breach, they came up with an efficient action plan and got in touch with the impacted consumers. Fortinet has been guiding them with apt risk mitigation plans since then. The cybersecurity vendor has also stated that there has been no sign of operational or financial impact around this data breach.
Other experts have shared that the leaked data not only contains customer information but also includes HR data, product information, marketing documents, employee data, and financial data for Fortinet. Experts believe that the data is not of much value. Otherwise, the hacker would have tried selling the data in the first place. As of now, Fortinet holds a neutral stature regarding the threat actor’s attempt to negotiate with the cybersecurity company against the accessed data.
The data that has been leaked on BreachForums touches upon Fortinet’s recent Lacework and NextDLP acquisition. The data also contains references to the Ukrainian threat outfit (DC8044). The data also hints towards an alleged history between FortiBitch and the Ukrainian threat group.
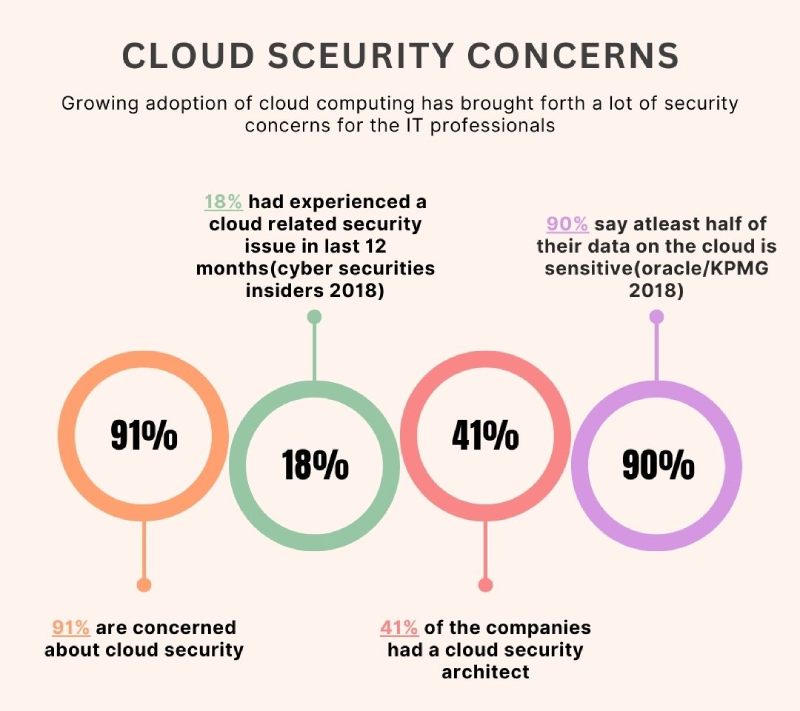
Heightened cloud data exposure risks!
The Fortinet data breach is not that huge in magnitude. However, such attacks are a stark reminder of the inherent cloud data exposure risks. Companies that leverage SaaS (Software-as-a-Service) but do not have adequate security systems in place are prone to similar cyberattacks. More often than not, enterprises prefer Google Drive for data storage with minimal or no protection at all.
There are basically three major cybersecurity blunders that SaaS-reliant enterprises commit. First, they don’t use MFA or Multi-Factor Authentication systems to secure access to their SaaS apps. Secondly, giving unrestricted access to employees and team members also leads to security issues. Lastly, storing sensitive and high-value data for a very long duration also makes them vulnerable to cyberattacks.
Experts are not yet sure about the exact process through which FortiBitch gained access to Fortinet’s SharePoint. However, they are working on a theory that revolves around the hacker getting access through legitimate login credentials through phishing. Then, the hacker might have logged in to exfiltrate the accessed data from SharePoint.
Revamped cloud security- The demand of the hour!
Experts believe that cloud security is something that needs a revamp. For example, developers should rely on encrypted storage, vaults, or environment variables to store sensitive data. Besides, it won’t be very wise to hardcode the credentials source code as well. Hardcoding access credentials such as passwords, API keys, and usernames into the source code and then unknowingly pushing them into some unsecured repository can enhance data accessibility.
First of all, companies must mandatorily leverage the MFA system to access SharePoint as well as other significant systems. Also, monitoring the repositories on a regular basis will be of great help and bring to the highlight any instances such as sensitive data, exposed credentials, and minor misconfigurations.
Experts also feel that companies should not totally rely on cloud service providers for cloud asset security. They must amp up their own security setups and implement phishing protection to guard against malicious attacks. Segregating less sensitive data from more sensitive ones will also reduce the risk of cyberattacks. Additionally, encrypting the data will further strengthen the layer of security.
The idea is to trust no one completely with your data, not even the cloud service providers.
Enterprises must work on developing a dedicated cybersecurity system to prevent any kind of data vulnerability. Investing in effective cybersecurity mechanisms to train team members from time to time can reduce the chances of a similar cyberattack to a great extent.