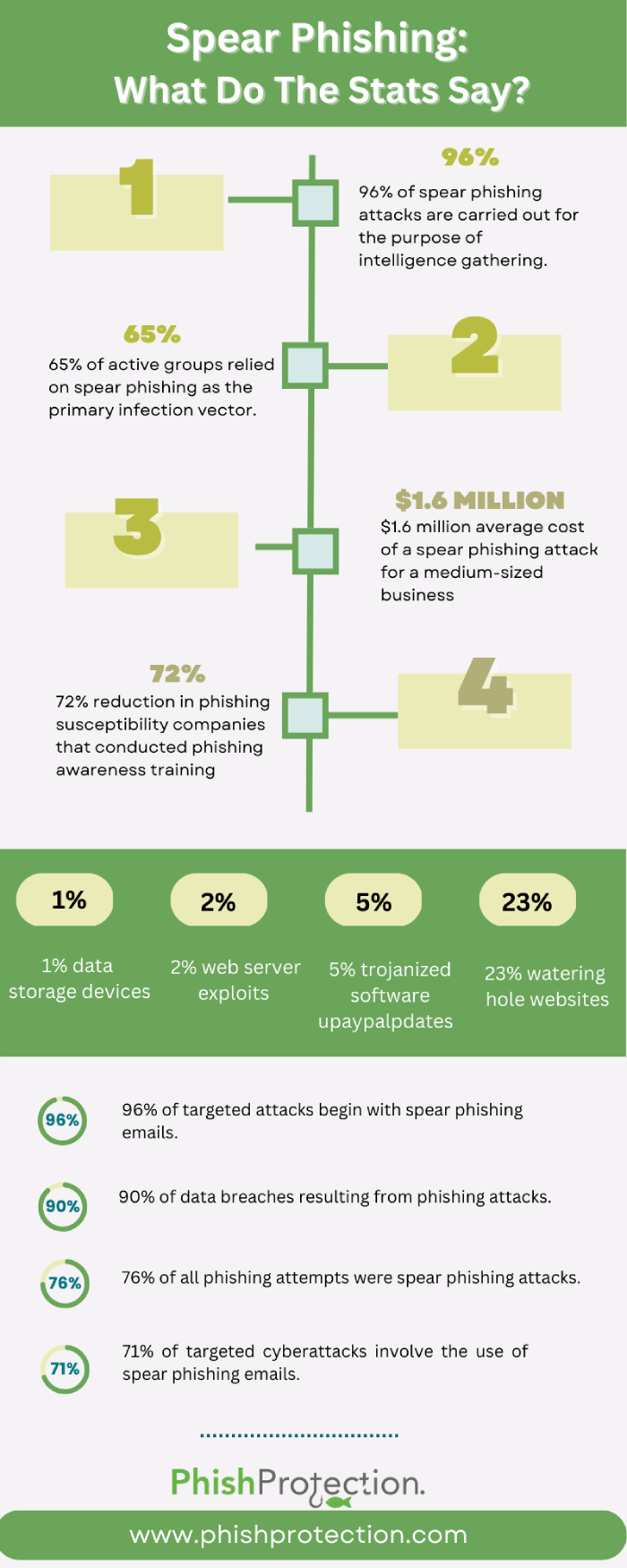
With advancements in technology, crimes like cyber theft, phishing, and scamming have increased over the years. American citizens lost over US$50 million due to phishing attacks in 2020, and for businesses, the figure is in billions.
Spear-phishing is one of the most perilous cyber-attacks methods that many organizations face in today’s world. Although phishing awareness at large has increased, spear-phishing victims often don’t realize that they have been targeted till they notice some unusual activity in their bank accounts or anywhere else. Spear phishing is not a stagnant form of a cyber-attack; it keeps evolving from time to time. Hence, it is inevitable that one is aware of the latest trends of spear phishing and how to manage the menace.
New Trends in Spear Phishing
Spear Phishing is evolving like any other method of cyber attack. And, today, there are new forms of spear phishing appearing on the scene and some old forms witnessing alarming growth. The following modes of spear-phishing mark the trends of the current time.
- Brand Impersonation: Emails are sent by impersonating famous brands, and the recipient is tricked into clicking on the link and typing in their organizational or personal logins. According to a statistical report published in July 2021, Microsoft, WeTransfer, DHL, and Google are the most commonly impersonated brands.
- Cryptocurrency-related Impersonation: Cryptocurrency-related scams have been on the rise thanks to this digital asset’s tremendous popularity in recent times. Attackers impersonate digital wallets and other such apps that inform the targets about a supposed security breach and lure them into disclosing their credentials.
- Business Email Compromise: In this form, the attacker impersonates an organization’s employee and requests information from another employee via email.
- Social Engineering: The age-old psychological manipulation technique remains relevant to this day, and threat actors continue to prey on the victims’ psychology to make them fall into making a mistake and divulge user credentials or click on a phishing link to install ransomware on their device.
Threat Actors Are Clever!
Today’s threat actors are clever and leverage the names of famous brands such as Google or Microsoft for their phishing and impersonation activities. Microsoft’s Office 365 suite and Google’s G Suite together constitute over 99% of the market share; hence it only makes sense for adversaries to take advantage of this, and these two remain among the top impersonated brands worldwide.
How exactly do they impersonate these brands? They send out emails that seem to contain links to download official documents but lead to downloading malware and ransomware on the individual’s device or stealing login credentials. It helps the attacker source out sensitive information and uses it to demand ransom.
Thus, it necessitates organizations to have state-of-the-art anti-malware and anti-ransomware solutions, besides email phishing protection tools.
More On Cryptocurrency-related Spear Phishing
Cryptocurrency-related phishing is the most recent trend in spear-phishing. With the rise of many organizations accepting money in the digital form, cryptocurrency has gained popularity in recent years. It has also shown a new path for malicious actors. They target individuals and send them emails that inform them that their digital wallet may have experienced a security breach and requires them to click on a link to safeguard their account again.
The situation puts the individual in a state of panic and then often clicks on the email link. While they attempt to login into their wallet via that link, the attackers steal their login details. The attackers may also encourage their target to buy a popular cryptocurrency such as Bitcoin or Ethereum or ask them to donate to a phony organization and steal their money and information once they enter their details on the payment page.
Anti-phishing Solutions You Need To Deploy
As spear phishing follows a path of fresh trends and practices, the ways of defense also need to be advanced and sophisticated accordingly. The following are some of the effective anti-phishing methods that protect against today’s most widespread forms of spear phishing.
Deploying Artificial Intelligence
Many AI programs in the market block spear-phishing attacks by recognizing malicious links and attachments. Google alone blocked more than 100 million emails containing scams in the year 2020. Some tools can help a user identify when any of their accounts may have been compromised.
Leveraging DMARC
DMARC or Domain-based Message Authentication, Reporting, and Conformance can protect email senders and receivers from phishing. The DMARC technical standard informs the recipient when the emails they have received do not pass the SPF or DKIM and suggests what to do in such a scenario.
Utilizing Multi-factor Authentication
The multi-factor authentication allows an account to be protected where logging into that account via a new device will require acknowledging several codes and one-time passwords that the user might receive on their email or phone number. It ensures that no one other than the rightful user can access the account.
Imparting Personnel Training
Training the staff in dealing with a potential phishing email is the best phishing protection that an organization can undertake. Be proactive about staff training and teach them how to recognize such emails and what to do if a suspicious email reaches their mailbox. Organizations must conduct investigations to determine whether any malicious emails with dubious subject lines have come to them. They can also implement technological solutions such as phishing simulations to assess employees’ current awareness levels and adopt robust business policies to ensure no confidential and sensitive data from the organization is being shared with outsiders.
Final Words
Spear-phishing is a specialized method of targeting an individual that the attacker has studied in detail. It helps them develop a strategy that, more often than not, might work on the target. Certain types of phishing links have shown more chances of being clicked, such as those posing some urgency. Hence, users must be cautious about suspicious links and learn to deal with them accordingly. Organizations have to be adequately aware and careful to sense the nuances in the realm of spear phishing to protect themselves using the right tools. Although the spear-phishing methods have evolved over the years, an organization can overcome most of its current trends with proper training and implementation of appropriate programs and policies.