Spear phishing, or targeted phishing, is an email scam aimed at a specific individual or company. These messages often pretend to be from a legitimate company or organization (such as your bank or internet service provider), and senders use personal information to gain access to accounts.
Spear phishing can be particularly dangerous, since the scammers generally know how to blend in, and their messages are crafted specifically to be convincing. Here are helpful tips for spear phishing prevention:
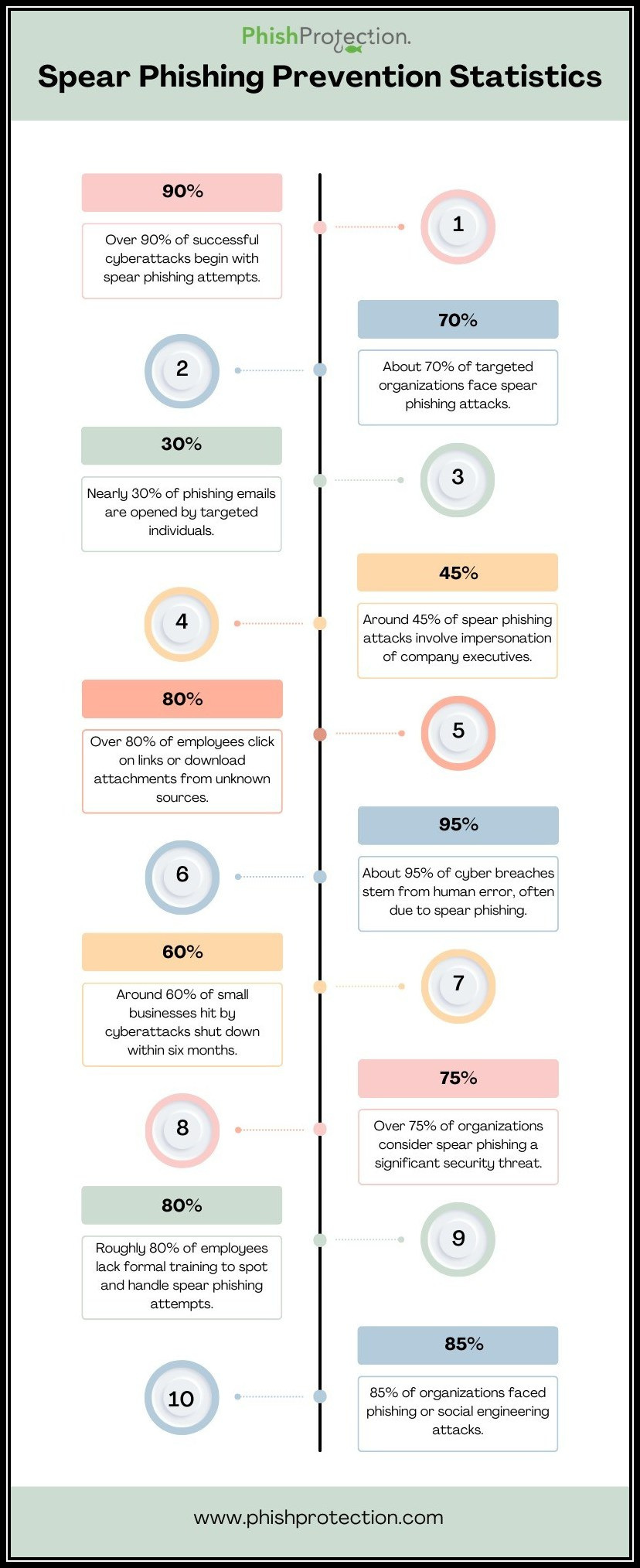
Spear-Phishing Definition
Spear phishing is a type of phishing attack that targets certain individuals or organizations typically through emails. The purpose of spear phishing is to steal sensitive personal information, such as login information or to gain access to the target’s device with malware.
While spear phishing emails are being sent, they attempt to do as much research as possible to bring assailants as close to their target as possible. The assailants come up with phishing messages using social engineering approaches in order to convince the victims to click on a bad link or attachment.
Once their target completes the desired activity, the attacker can gain access to their credentials and assume control of your network behind the scenes.
Spear-phishing vs Phishing vs Whaling
Phishing, spear-phishing, and whaling are malicious mails that are designed to resemble the fair usage of a type of cybercrime.
Phishing
Where quantity is concerned, phishing attacks are centered around quantity. The e-mails, tweets, and texts relaying a fraudulent message may be generic, but it’s sent in large quantities to a large group of different clients to increase the odds of catching a victim.
Phishing attacks through phone calls are often known as vishing for voice-phishing. And phishing attacks through text messages are known by the name of smishing for SMS-phishing.
Spear-Phishing
Spear-phishing attacks prioritize quality. Spear-phishing emails, texts, or phone calls are highly customized for a specific organization or individual. Spear-phishing attacks are more likely to deceive their potential victims because of the time and effort spent creating customized texts that appear to come from the legitimate sender.
Whaling
Whaling attacks follow precisely the same individualized strategy of spear-phishing attacks. Whaling brokers prey on high-level targets to capture financial and privacy-invasive information. To address the imbalance regarding the value of their information, to engage in targeted killing, whale hunting often results in huge measures of damage.
How A Spear-Phishing Attack Works
The explanation behind spear phishing attacks’ unique level of personalization enables them to be extremely dangerous and straightforward to fall into. Hackers rely on reconnaissance tactics during their research so they can increase the chances of success.
Social media platform users frequently use Facebook and Linkedin to stalk their targets. By drawing a map of their personal contacts, they seek a picture of their target’s social network, which provides them with ample context in order to properly craft their persuasive message.
More sophisticated hackers may use machine learning algorithms to analyze huge volumes of data in an effort to reveal specific persons who are most vital.
Utilizing your personal information, spear phishers can then craft a seemingly genuine email that grabs your target’s attention. Many people don’t recently update their security because they feel pampered by a personal touch and aren’t as careful about clicking a link or downloading an attachment. However, this mistake can result in major consequences, such as the theft of private information or a malware infection.
Prevention Tips
Your personal computer’s popup screen can play tricks on you. Keep yourself updated about the dangers the information we offer to you can bring.
- Unusual sense of urgency.
- Incorrect email address.
- Spelling or grammar mistakes.
- Sensitive information is requested.
- Links to un-matched domains are included.
- Includes unsolicited attachments.
- Attempts to panic the recipient.
To prevent any sort of phishing attack, comprehensive security awareness training is vital, regardless of whether an employer is training many users from home. But even security-conscious employees will sometimes click on a malicious link, whether they’re rushed or it was really convincing.
In conclusion, Spear Phishing Prevention refers to the technique of targeting an organization or person by impersonating someone with higher authority. This is achieved by using emails with false information. Entrepreneurs and organizations should adopt phishing protection techniques to safeguard their businesses from Spear Phishing.