With threats such as ransomware, phishing emails, and malware constantly lurking in the dark, cybersecurity experts are always at war against those waiting to exploit uneducated victims. Since the first phishing attack in the mid-1990s, it has evolved into a highly sophisticated and most frequent attack vector leading to fraud activity. Enterprises need to fundamentally change their approach to cybersecurity and align their budgets with the newly defined reality. As per a report, cybersecurity expenditure will touch approximately $6 trillion by 2021 globally.
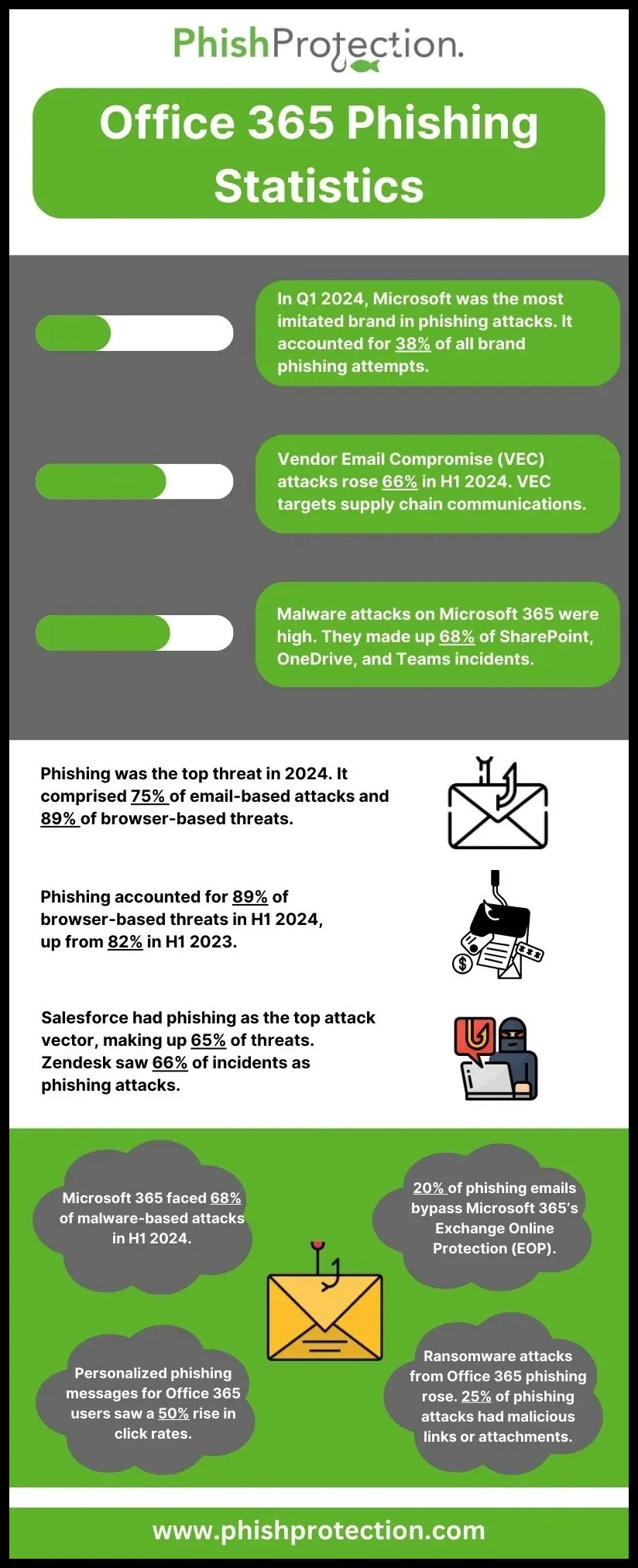
Statistics show that ransomware attacks increased in 2020 by a massive 62% since the previous year. 74% of American organizations suffered phishing attacks in 2020.
Decoding The Numbers in The Phishing Landscape
Although organizations are deploying considerable resources to enhance their cybersecurity posture, they still have a long way to go. Here are a few statistics:
- The COVID pandemic made many employees shift their work from typical office cubicles and offices to home. While the disease was already scary enough, threat actors leveraged it to attack the vulnerable networks in personal homes.
- Malicious actors infiltrate the enterprise network through their weakest link, the employees. Human error remains one of the prime reasons behind data breaches.
- Most enterprises, even the big tech organizations like Facebook, Equifax, and Capital One, took more than six months to detect a data breach. Crucial information like SSNs, credit card details, and passwords might already be compromised till then.
The Human Part of the Puzzle
The above section discussed some glaring statistics about the rising number of phishing and data breach attempts, implying the need for businesses to adopt robust anti-phishing and anti-ransomware solutions. What’s important to note from these statistics is that the most crucial part of solving the cybersecurity puzzle is the human element. These attacks are successful primarily due to the error in human judgment involved as they interact with various aspects of information technology.
A well-educated user is the best preventive measure against any phishing email.
Providing constant phishing awareness training to users using the latest resources and methods goes a long way in improving the overall cybersecurity posture for any organization. The latest development from Microsoft, known as Office 365 Advanced Threat Protection, has introduced some new anti-phishing tools. One such tool is the Phishing Attack Simulator, which allows security administrators to run mock security attacks on users. The simulation reports can then analyze their awareness and understand the organization’s vulnerability against such attacks.
Phishing Attack Simulator
The Phishing Attack Simulator is an anti-phishing resource that helps security administrators and organizations to train their employees against phishing emails and ensure email phishing protection. It is a great exercise to rectify unhygienic behavioral traits and establish reasonable and educated cybersecurity responses.
Advanced Threat Protection allows administrators to use the attack simulator and help users become more defensive and vigilant against phishing emails that may lead to grave consequences.
How to Launch a Phishing Attack Simulation?
Following are the steps to successfully create and launch a Spear Phishing Attack Simulation.
- First, visit protection.office.com.
- Next, click on “Threat management” in the left menu.
- Now, select “Attack simulator” from the drop-down list.
- Now, click on “Spear Phishing Attack.”
- Give a custom name to the attack.
- Next, click on “Select template.”
- Proceed to select a template and click on “Next.”
- Now, choose the targets to be attacked and click on “Next.”
- Now, set up the fake email details such as:
- From (Name)
- From (Email)
- Phishing Login Server URL
- Custom Landing page URL
- Subject
- Next, click on “Next.”
- Edit the template with the WYSIWYG or HTML source and click on “Next.”
- Finally, click on “FINISH” to start the attack simulation.
For detailed instructions, you can visit here. Besides, if you want to launch a more comprehensive phishing attack simulation on your organization, you can have a look at Microsoft’s official website.
What Do The Results of The Phishing Simulation Show?
The administrator will receive a notification once the attack is launched and also when the attack is completed.
- The results are found in the attack simulator option under the security and compliance center. The simulation results present a detailed report that security administrators and organizations can further study.
- The report displays the total number of targeted users in the phishing attack simulation. It also shows successful attempts, meaning the number of users who clicked the link and entered their credentials.
- The success rate denotes the percentage of users who clicked the link and entered their credentials, falling prey to the attack simulation.
- Finally, the report presents a detailed list of users who fell prey to the attack simulation with the credentials and time of clicking the links.
What Does This New Tool Mean For Businesses?
Several small businesses keep using outdated or least-protected tools that increase the attack surface of the organizations. At the same time, phishing simulation tools may not be very economical for many of these SMEs. Microsoft did a great job by offering these tools at affordable and accessible levels to the organizations that can use these tools to provide the best phishing protection. However, email admins must remember that no single system can be considered an all-in-one/ one-for-all solution. The right approach to building a robust cybersecurity infrastructure is to create multiple protection systems at various layers.
This tool can help organizations in two ways.
- Firstly, it can allow security administrators and organizations to identify vulnerable users or employees who need attention and training.
- Secondly, it will enable organizations to ensure that there are no vulnerabilities from within through behavioral training of the employees.
As a result, this tool will considerably help organizations (whether big or small) improve their email security infrastructure.
Final Words
Technology is evolving by leaps and bounds, but so are the methodologies of threat actors to target organizations. The best defense for organizations is to stay alert and avoid falling prey to these attacks by training their employees to be more vigilant. Accordingly, the Phishing Simulation tools can prove highly advantageous to businesses, especially SMEs, to keep malicious actors at bay and reduce data leakage due to phishing scams.