As the world transforms into a more digitally connected environment, the risks have also amplified manifold. New York-based domain and web hosting service provider GoDaddy discovered an enormous security breach on November 17 this year, which affected almost 1.2 million accounts. The incident occurred when the attacker accessed the GoDaddy network through a compromised password on September 6, 2021. The incident filed with the Security and Exchange Commission (SEC) states that the organization had observed and identified “suspicious activity” in the hosting environment that managed WordPress. The IT Security team undertook immediate action, but the malicious actor had at their disposal almost two months to establish a rigid presence by that time. GoDaddy stated that anybody using WordPress currently should assume as compromised if not proved otherwise.
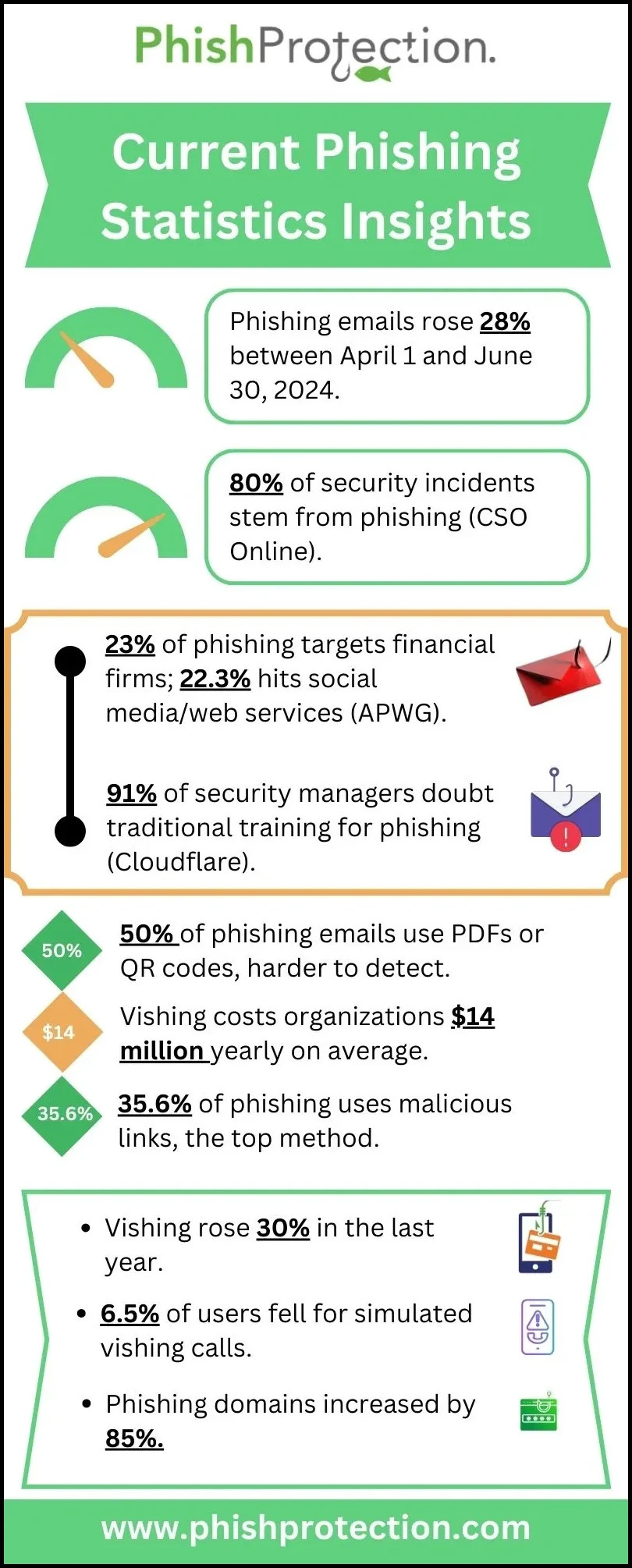
Phishing Statistics To Reflect On
The world of phishing has seen a dramatic rise over the years.
The above graph illustrates the number of brands and legitimate entities targeted by phishing attacks from January 2009 to March 2021. As the world becomes more tech-reliant and transactions and communications become more accessible, malicious attempts to disrupt and intrude into information networks and databases have also increased.
The Modus Operandi of the Phishing Attack on GoDaddy
As suggested in the report filed with the Security and Exchange Commission (SEC) and mentioned previously, the illegal access was gained through a compromised password, after which the attacker established a strong presence in the GoDaddy Hosting Environment. The situation enabled the third party to gain information about WordPress Admin passwords and sFTP database username and password for active customers. A few of the active customers had their SSL private keys exposed too. The total of 1.2 million accounts was a mix of active and inactive customers. Along with the information mentioned above, email addresses and customer telephone numbers were also exposed.
The Aftermath
The Chief Information Security Officer (CISO), Mr. Demetrius Comes, had stated that they discovered the breach much later, though the action was immediate. They are currently investigating the entire matter with the help of an IT Forensics firm and Law Enforcement. GoDaddy has also gone ahead and reset all the passwords of the accounts that were affected. It has also declared a warning of future phishing attacks, and users are advised to take standard precautions like installing or updating anti-malware and email phishing protection software.
Earlier Examples of Phishing Attacks on GoDaddy/WordPress
The above is not the only phishing incident targeting GoDaddy. A similar incident occurred last year, whereby fraudsters redirected email and web traffic destined for several cryptocurrency trading platforms for a whole week. The entire exercise was directed towards GoDaddy employees. It was discovered in April 2020, though the first attempts were made way back in October 2019. The scam allowed the intruders to get control over more than half a dozen websites of repute, including escrow.com. They were also able to read the internal notes that GoDaddy employees had left on customer accounts.
In March 2020, there was another widespread voice-phishing (vishing) attack on GoDaddy wherein the perpetrators tricked the employees over the phone to transfer ownership of domains to fraudulent accounts. The main aim of the malicious actors has been to gain illegal access to cryptocurrency domains and change the settings.
A 2020 Phishing and Fraud Report stated that “almost 10% of all phishing incidents involved victims being sent to malicious pages built using WordPress”. The report also pointed out a steady increase over the years. The Wordfence WordPress Threat Intelligence Report for 2020 stated that it blocked almost 90 billion malicious log-in attempts from over 57 million unique IP addresses.
Ways to Counter Phishing and What Should Organizations Do to Mitigate The Menace?
Countering phishing attempts needs to be a multi-pronged effort. Along with implementing robust anti-phishing solutions and other safeguards, adequate awareness by every individual is also essential, as elaborated below.
Email Security
If you know how to stop phishing emails, you will be able to control a great deal of phishing, as a common channel used by malicious actors for phishing is the ubiquitous email. Electronic mail has become the favorite mode of communication in recent times, and even though it is easy and fast, it is vulnerable. Organizations will have to invest in the best phishing protection available in the market to build resistance to phishing emails and keep their data and information safe. There are myriad options available, and a little bit of research is required to understand the organization’s needs. Anti-malware and anti-ransomware solutions should top the list of must-haves.
Round-the-clock Vigil
Advancements in technology have transformed most of the daily human activities. However, the flip side to it is the constant war being waged by threat actors to enter the sanctum sanctorum of organizations and access data, which otherwise would be unavailable to them. Stopping them would be the IT Security teams of those organizations, which must be vigilant forever. Though some systems and tools act as force multipliers, the individual will also be alert throughout. Constantly monitoring the network and keeping an eye on the internet traffic is essential to counter any phishing attempt or illegal entry.
Awareness & Adequate Training
Finally, the most robust defense of any organization is also its weakest: people. Employees must undergo rigorous awareness training through phishing email examples and methodologies like those employed by malicious actors to penetrate vulnerable systems and firewalls. They will also have to be trained in identifying phishing attempts. With the world of phishing diversifying into many forms, the training must be up to date and suited for the present and apparent threats.
Final Words
The GoDaddy saga is an urgent reminder of the constant threats emanating from the virtual world. The hosting and domain giant does have a robust online security system to create firewalls. However, malicious actors are always hunting for vulnerabilities and on the lookout for their next phishing victim, and all they would need is to be lucky once. The virtual world is also an ever-changing entity with constant transitions of technologies. Amidst such a cauldron of activity, vigil must be heightened to the maximum extent.