If you oversee the information security services and administration of the networks in your organization, then it is your responsibility to safeguard the users in your system from phishing and other attacks that can disrupt the services. There is no need for complacency in the digital age, and you can never feel 100% protected as hackers keep inventing new techniques and innovative ways to exploit vulnerabilities of user’s information systems. So if you plan to combat one threat and are successful in protecting yourself, they will find another way to invade your security periphery. Hence, phishing protection is an ongoing job as you always need to keep an eye on your defense strategies and be on a lookout for any system vulnerabilities- human or technical.
Best Practices for Phishing Protection by Organizations
Always Stay Away from Suspicious Emails, Links and Attachments
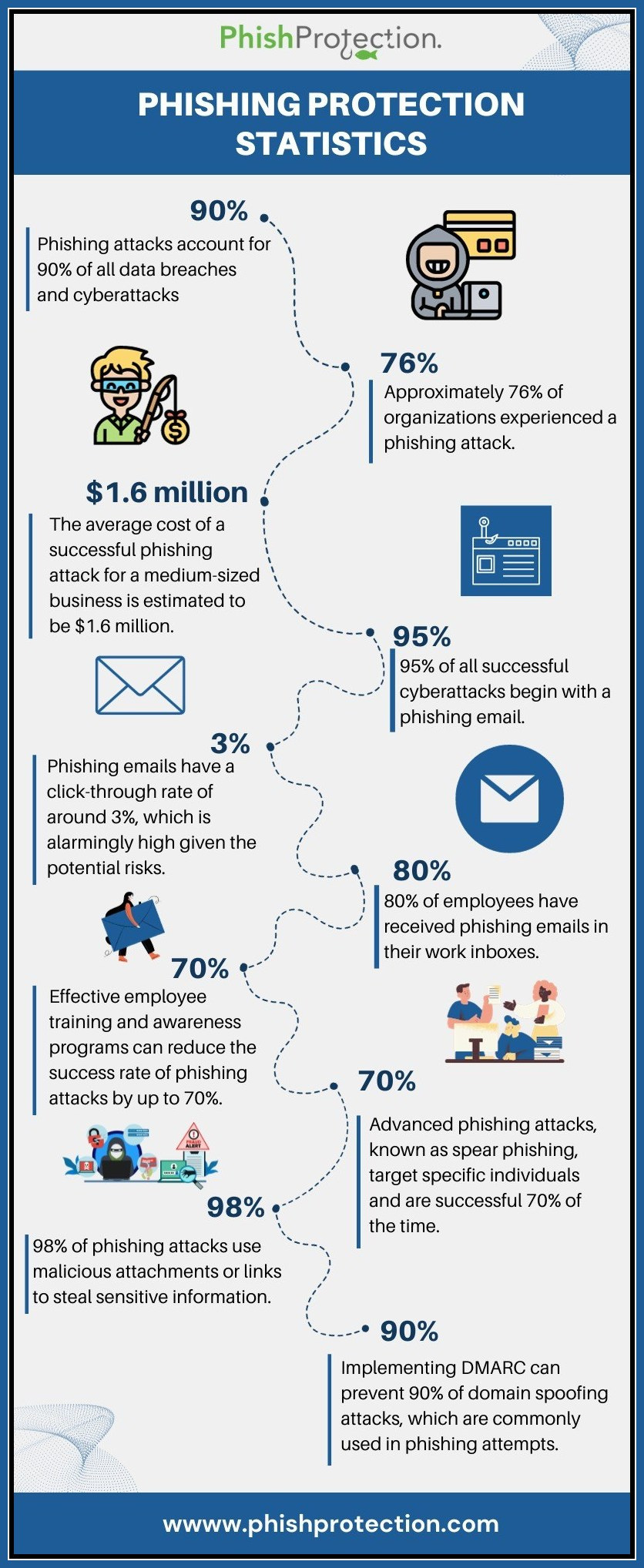
Almost 80-90% of attacks from cybercriminals start from a phishing email. Yes, if you are not sure about the sender of an email or if you are suspicious of an email, it is always good to not open that email or better still, delete the email. Attackers know precisely how to lure you into opening an infected email by using an attractive email subject.
Most of these emails say that you have won some prize or you have a discount coupon waiting for some ‘X’ amount of dollars etc. If you get hooked to the subject and by any chance, open the email and click the links in the email, you are inviting yourself to an imminent phishing attack. Sometimes you never know that your computer is infected and it may even start acting as a bot to carry out espionage or cyber warfare activities hidden beneath the surface.
Use a Trusted Antivirus
The importance of an efficient Anti-virus cannot be under-estimated when it comes to protecting your company from cyber espionage. The anti-virus must be a trusted one like Kaspersky, MacAfee, etc. and should have e-mail scanning feature. Also, don’t go for free ones. A small investment in a good anti-virus will go a long way in protecting you from phishing attacks.
Employ SPF protection
SPF (Senders Policy Framework) is an email authentication methodology that helps in detecting forged email addresses and block spoofed emails. Through the implementations of SPF policies, enterprises can ensure that phishing is contained to some extent.
Every email is filtered and only if it received from an authorized list of domain names, is it allowed into the system. An SPF system is employed in two parts:
- SPF Checking: Allows the organizations to determine the legitimacy of an e-mail.
- SPF Publishing: Assists in determining the optimum e-mail server for sending enterprise e-mails.
Report Suspicious Activities
Whenever you spot a suspicious email or an attachment, it is vital to report it to the concerned authorities so that immediate action is taken. The quicker you inform, the quicker will be the preventive measure taken to contain the attack and prevent those emails from infecting your organization’s computers.
Frequent Update of Company Security Policies
It is imperative to have all your policies and procedures related to the security and protection of confidential data, maintained properly in your organization. Ensure you follow stringent backup policies so that you can quickly recover any data lost due to a phishing attack. It is also essential to follow dual-control techniques when it comes to protecting critical data assets of your organization.
Avoid the use of Removable Media
You are free to use all kinds of removable media like SD cards and USB drives for your personal use, but when it comes to enterprise security, network administrators must prevent the use of such removable media. Because these media are highly prone to malware attacks and if you are in an urgent situation to use it, better have them completely scanned before using and after using them.
Corporate Training
Prevention is better than cure, and hence, every organization should implement some corporate training to increase the awareness of phishing attacks amongst their employees. Even though it is not the best phishing protection as all it takes is a single click of an infected link from one employee, and your whole network gets busted. But still, training helps in making the employees aware of the threats posed by these cybercriminals and how to safeguard yourself from these phishing attacks.
Conclusion
The global information-age brings with itself, many advantages. Increasing use of digital media by businesses is in vogue these days. However, it also poses a few risks where cybercriminals are always trying to invade your systems and steal your private information. Use the safeguards mentioned above to prevent these attacks from affecting your business operations.