Amazon blocks 1,800 alleged DPRK IT fraudsters—Experts hint at a massive cyber trend!
State-sponsored IT fraud is a real threat, and the recent disclosure by Amazon further proves the point. The e-commerce giant has barred a whopping 1800 DPRK IT operatives from joining the company since April 2024. This cyber incident is a staggering reminder of how persistently bleak the situation can be when it comes to state-sponsored threat actors.
The Chief Security Officer and Senior Vice President at Amazon, Stephen Schmidt, has revealed that there has been a 27% quarter-over-quarter boost in applications from DPRK-affiliated threat actors in 2025. IT scams are definitely not a new entry in the cybersecurity landscape.
However, the obsession of the cybercrooks with a single company- Amazon- may come off as unnerving. When the same kind of attacks are being orchestrated strategically against the same organization, it is a clear indication of a large-scale industrial operation carefully strategised to create national implications.
The IT worker scam!
The IT operative scam involves fraudsters who operate on behalf of a nation-state. They serve as legitimate remote technology manpower to secure legal jobs on foreign soil. Cyber experts believe that although different nations are involved in such activities, North Korea is a key suspect.
The motivation behind such malicious approaches includes cyber espionage and obtaining indirect financial contributions for sanctioned activities.
Amazon’s workforce is global. But a whopping 1800 malicious attempts from the same country, trying to infiltrate the company, is indeed a case of concern. It also hints towards the possibility that other companies might be going through the same without even realizing it.
How does Amazon detect DPRK applicants?
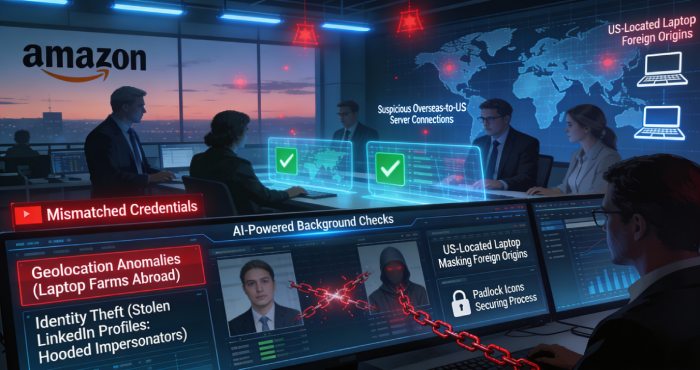
Amazon has an intricate, multi-layered hiring strategy. It is the ultimate blend of automation and human intervention. Amazon’s rigorous hiring strategy includes stringent credential verification, well-structured interviews, and AI-powered background checks. All these components work in unison to detect inconsistencies in the screening and recruitment process.
It is because of this advanced hiring strategy that Amazon got to discover priceless insights around DPRK-backed IT operatives and their tactics. Deeper analysis has revealed that identity theft is one of the most prevalent and highly sophisticated threats nowadays. These state-sponsored cybercrooks very easily impersonate real employees, maybe software engineers, to break into inactive LinkedIn accounts. They also misuse legitimate, active profiles to look more credible.
Another tactic being used by these state-sponsored fraudsters is leveraging laptop farms. Generally, physical laptops are stored within the USA borders to bypass geolocation checks. They create a fake impression of being employed within the USA, all the while operating from overseas.
Apart from conventional software engineers, hackers are now also targeting professionals across other roles, such as machine learning and artificial intelligence experts. The main reason for targeting these professionals is their high paychecks, easy access to data, and sensitive intellectual property.
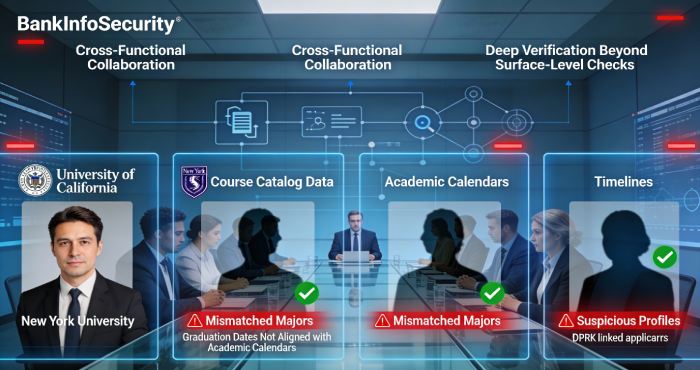
A common trend among these fake IT applicants is flaunting educational connections with universities in California and New York. A detailed investigation is required to address discrepancies, such as mismatches between stated majors and the courses offered by the mentioned universities. Close scrutiny also helps unravel minute discrepancies such as non-alignment of graduation dates and academic calendars.
These strategic attack patterns have helped business organizations realize that surface-level checks are no longer adequate in these times. Cross-functional collaboration and contextual awareness are required to hire the right people and prevent any malicious recruitment.
It is not limited to just Amazon
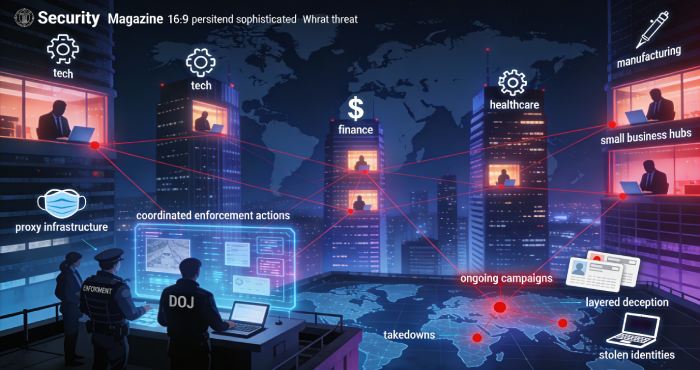
Amazon is not the only one facing the brunt of this nation-state threat campaign. Cybersecurity experts and law enforcement agencies have been quite vocal about such attacks across different industries. The US Department of Justice has carried out multiple intensified enforcement efforts targeting fraud networks that used to help DPRK operatives secure employment opportunities in different US-based organizations.
A group of researchers at Sophos has concluded that such threats have become incredibly common across small enterprises and Fortune 500 companies. What’s more concerning is that the attacks are not slowing down even after increased awareness among the business organizations. Every malicious campaign is being structured with sophistication- proxy infrastructure, layered deception, and stolen identities make things worse.
Cybersecurity awareness and a strong security framework are more critical than ever, and Amazon’s disclosure has reshaped where cybersecurity responsibility truly begins. What was once seen as purely an HR concern has evolved—driven by AI-powered threats—into a frontline security issue, making hiring a potential attack surface. Integrating cybersecurity controls, including phishing protection, into every stage of the recruitment process is now essential to safeguard organizations.
With a remote work culture and global hiring, things will only get worse. The only way out is to blend cybersecurity systems into every layer of the recruitment process. It is important to understand that even a simple job application can be as dangerous as a phishing email.