Phishing attacks and web application threats are hitting more sites every year. With ninety-eight percent of web applications showing weaknesses, attackers have no shortage of targets. Here’s what you need to know and the steps you can take to keep your website and users safe.
Spotting the Weak Spots: Common Threats
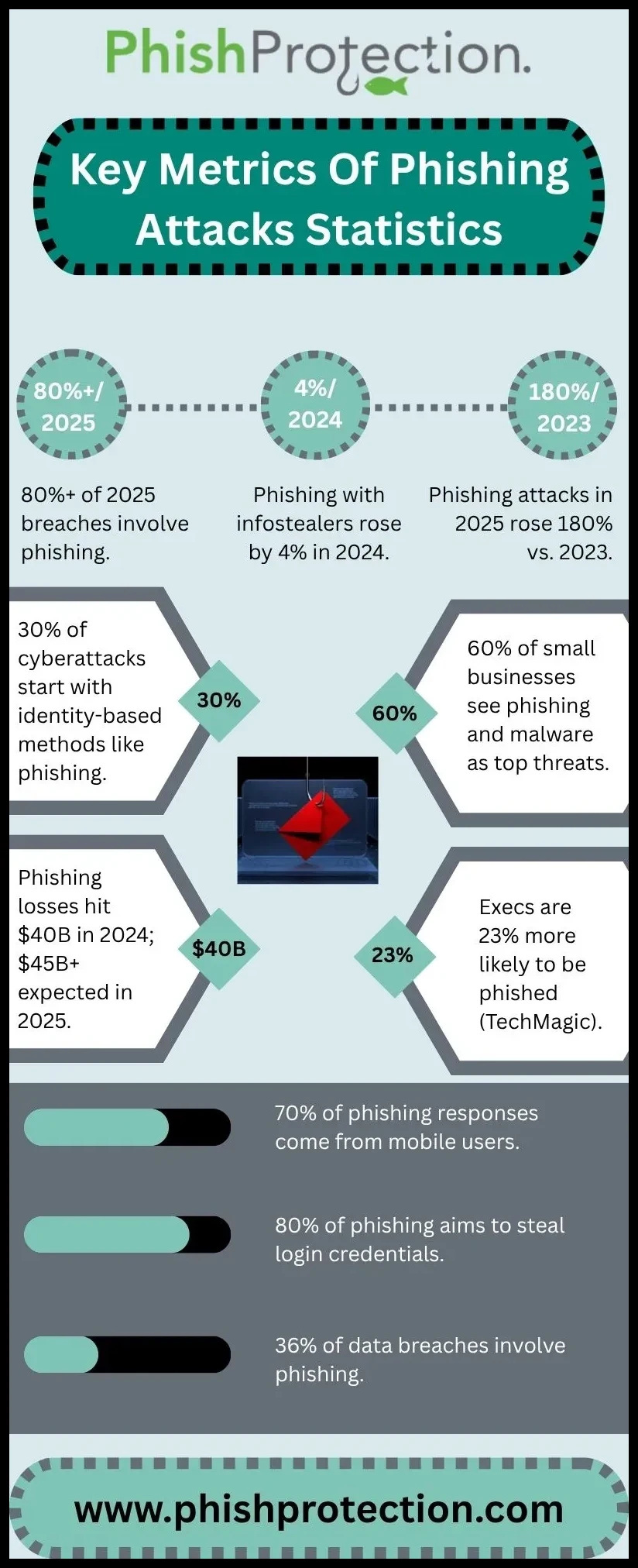
Almost every website has open doors if the basics are not covered. Phishing, ransomware, and botnet attacks are all common outcomes of these gaps. Last year, almost fifty-four people every second were hit by a cyber attack. In 2024 alone, there were over 1.5 million attacks that took aim at the domain name system. If your website’s security is not kept current, it stands out to attackers.
Password habits remain a weak defense. Forty-four percent of people still recycle passwords across accounts. This increases risk, as one leak can lead to more accounts being compromised. Many threats also start with phishing emails. Business email scams took in over fifty-five billion dollars in the last ten years. Company accounts can be broken into with a single successful fake message.
Real-World Risks: Hosting Choices and Phish Attacks
Many attacks start by targeting loopholes in hosting platforms or misconfigured accounts. Weak controls and patchy maintenance can open the way for phishing or bot-based threats. For example, some businesses using low-cost shared plans skipped security updates, which later let attackers slip in through outdated plugins.
Choosing well-maintained services helps. Premium WordPress hosting solutions, managed cloud options, and specialized site management firms offering built-in updates, server monitoring, and strong account isolation lower many risks. WordPress hosting, managed cloud options, and specialized site management firms can all make it harder for phishing attacks to succeed as long as security settings are kept current.
Fast Moves: Modern Attack Speed and Shifting Tactics
Attackers do not take long to act. The fastest known electronic crime breakout took only fifty-one seconds. Most malware detected in 2024 was not even real software but used other sneaky methods to fool users. Phishing attacks get more advanced each year and can be tough to spot without training and proper tools.
Once a website or email account is breached, attackers can quickly spread malware, steal money, or use your site to target others. The odds of getting stolen funds back are very low. Police and other authorities recover around two percent on average.
The Cost of Letting Your Guard Down
Cybercrime comes with heavy price tags. The expense worldwide is forecast to pass twelve trillion dollars by 2025. That is about thirty-three billion each day. Small and medium businesses are hit hard. In Canada and Mexico, more than two-thirds of these businesses reported cyber attacks in the past year. Healthcare and retail sites are also common targets, with automated attacks using bots up by sixty percent and every major healthcare site facing these problems.
A phishing attack can be the start of a run of trouble. After a breach, it can take up to 258 days on average to spot and deal with the damage. The largest hack so far hit over three billion user accounts. Most can trace at least some of the problem back to a simple phishing trick or weak password.
Good Habits for Stronger Defense
Security is not one thing but a set of habits. Here are steps that reduce your risk without adding too much work:
- Use unique passwords for every account. Long phrases work best.
- Update site software and plugins as soon as patches come out.
- Turn on multi-factor authentication wherever possible.
- Run training sessions for staff so they know how to spot risky emails and websites.
- When creating websites, ensure security measures are integrated from the start to prevent vulnerabilities.
- Use security tools that check for malware-free attacks since most threats now do not rely on obvious downloads.
- Regularly back up everything on your site and store backups safely.
- Secure every application programming interface your site uses, as these are seeing more focused bot strikes.
- Research hosting services that offer ongoing maintenance, built-in security, and fast support.
Supply Chains and Third-Party Risks
Even if your own systems are strong, vulnerabilities in your supply chain can be exploited. By next year, nearly half of global companies may see supply chain incidents. Review which companies have access to your data or website and ask how they keep things safe. Missteps like a tracker error in a web tool once led to a breach that affected almost five million people in one case alone.
Don’t Wait for Recovery
Relying on law enforcement to get back lost money or data is not realistic. Only a tiny share ever returns. Prevention is much less expensive. Security experts suggest reviewing your policies often, checking logs every day, and building a habit of doubting odd emails or login requests.
A Final Word: People Still Matter Most
Ninety percent of breaches come down to user actions. Even advanced tools help only if people use them well. Set clear rules, keep training current, and keep software up to date.
Ninety percent of breaches come down to user actions. Even advanced tools, including phishing protection solutions, help only if people use them well. Set clear rules, keep training current, and keep software up to date.
Most attacks succeed because of one small gap, not a grand scheme. Stay alert, choose strong hosting, and make good security a routine part of running your website.