Ransomware Attack Freezes Jackson County, GA Government Systems
9th March 2019 | Place: Jackson County | Reported Here
A little over a week ago government computer systems in Jackson County, Georgia were hit with one of the most sophisticated ransomware attacks attempted in the US. After a week with their entire computer and internet network down, they’ve decided to cough up $400,000 to regain control of their systems and to retrieve stolen files.
FTC Warns Users Against Online Dating Scams!
13th February 2019 | Application: Tinder | Reported Here
A new notice released Tuesday by the Federal Trade Commission highlights a surge in ‘romance scams,’ or scenarios where scammers trick love-lusting internet users into sending them money, only to later disappear.
The scams cost victims an astonishing $143 million in 2018, up from $33 million the previous year and making it the most costly type of consumer fraud reported to the FTC.
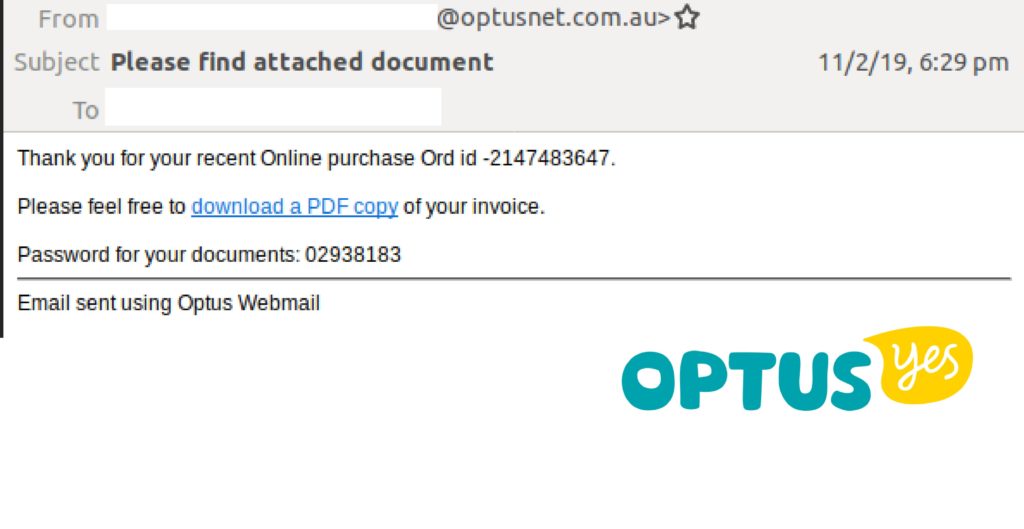
Optus Email Scam
8th February 2019 | Site: Optus | Reported Here
Optus customers have complained of being caught up in a major security breach after they tried to login to their account and found themselves signed in as Vladimir.
Users say their screen kept refreshing on a loop and one person reported receiving an e-mail with a vastly inflated bill.
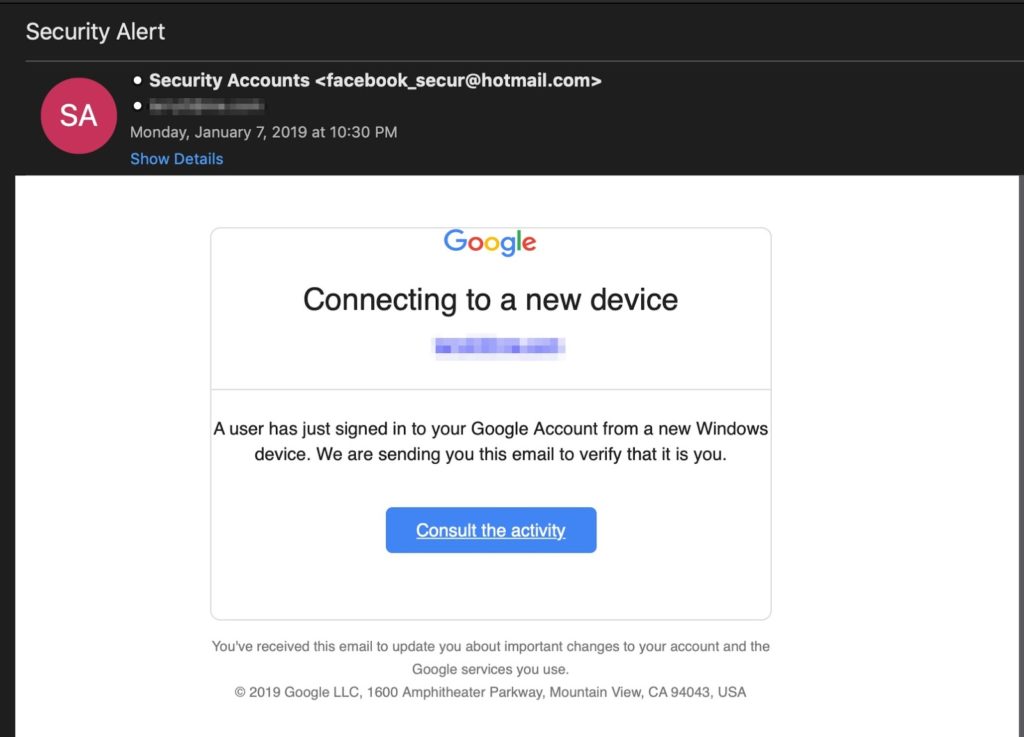
Google Translate Phishing Attack
5th February 2019 | Site: Google | Reported Here
This week, a security researcher at Akamai outlined a novel phishing approach that they recently encountered in their inbox that attempts to use Google translate links to mask disreputable links.
In January, the researcher received an email informing them that someone had attempted to access their Google account on an unrecognized Windows device.
Tecnimont Pvt Ltd Attack
10th January 2019 | Site: tecnimont | Reported Here
Attackers forwarded emails to the leader of Tecnimont Private Limited in India which is an Indian subsidiary of the multinational group Tecnimont.
In the emails, the hackers impersonated global C.E.O P. Folgiero and succeeded in convincing the Indian head that a money transfer from Italy was unable to be carried out because of problems with the regulator. They impersonators gave further instructions to make separate transfers to another bank account in Hong Kong.
The money was subsequently transferred from India to the Hong Kong account and withdrawn within moments of the transfer. 18.6 million dollars was lost from the Indian arm of the company due to this simple oversight.
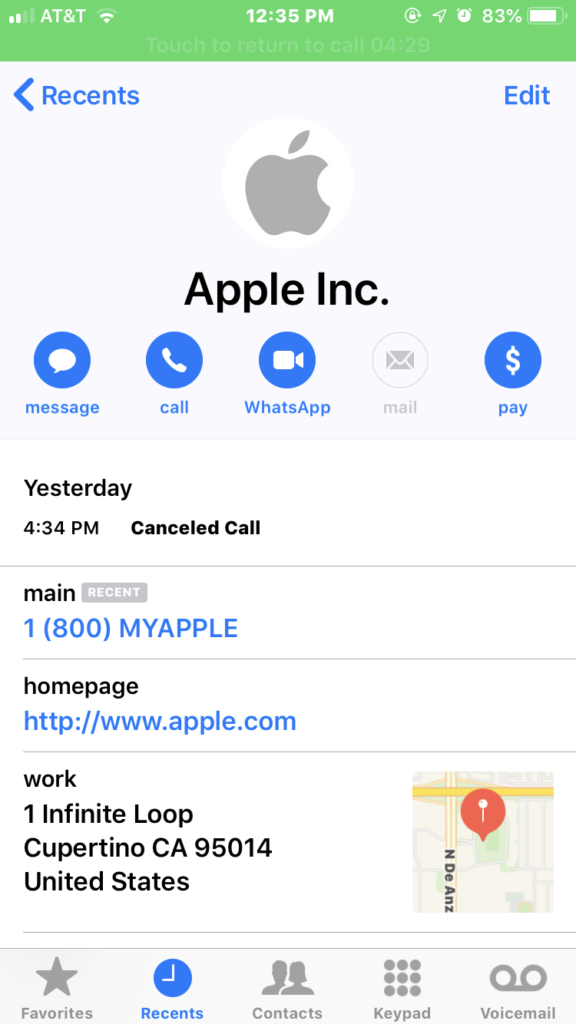
Highly Sophisticated Apple Vishing Scam Detected
8th January 2019 | Company: Apple | Reported Here
A sophisticated Apple vishing scam has been uncovered. In contrast to most phishing attempts that use email, this scam used voice calls (vishing) with the calls appearing to have come from Apple.
The scam starts with an automated voice call to an iPhone that spoofs Apple Inc. The caller display shows that the call is from Apple Inc., increasing the likelihood that the call will be answered. The user is advised that there has been a security breach at Apple and userIDs have been compromised. Users are told they should stop using their iPhone until the problem has been resolved. They are asked to call back Apple support for further information and a different telephone number is provided for this purpose.
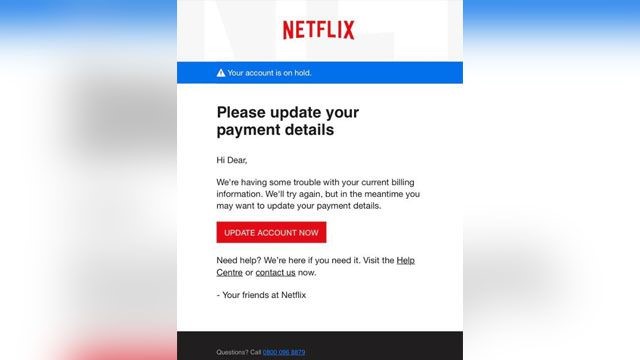
Netflix Phishing Attacks
26th December 2018 | Site: Netflix | Reported Here
A new bulletin issued by the Federal Trade Commission highlights a fresh wave of Netflix phishing scams that have been landing in email inboxes around the globe.
The scam itself is old. It’s a classic “update your payment information” request that includes a link to a fake Netflix login screen where gullible folks might enter their details, and it’s the kind of thing that we see pretty regularly in our spam filters and junk mail folders, but this particular scam is apparently widespread enough to have drawn the attention of the FTC.
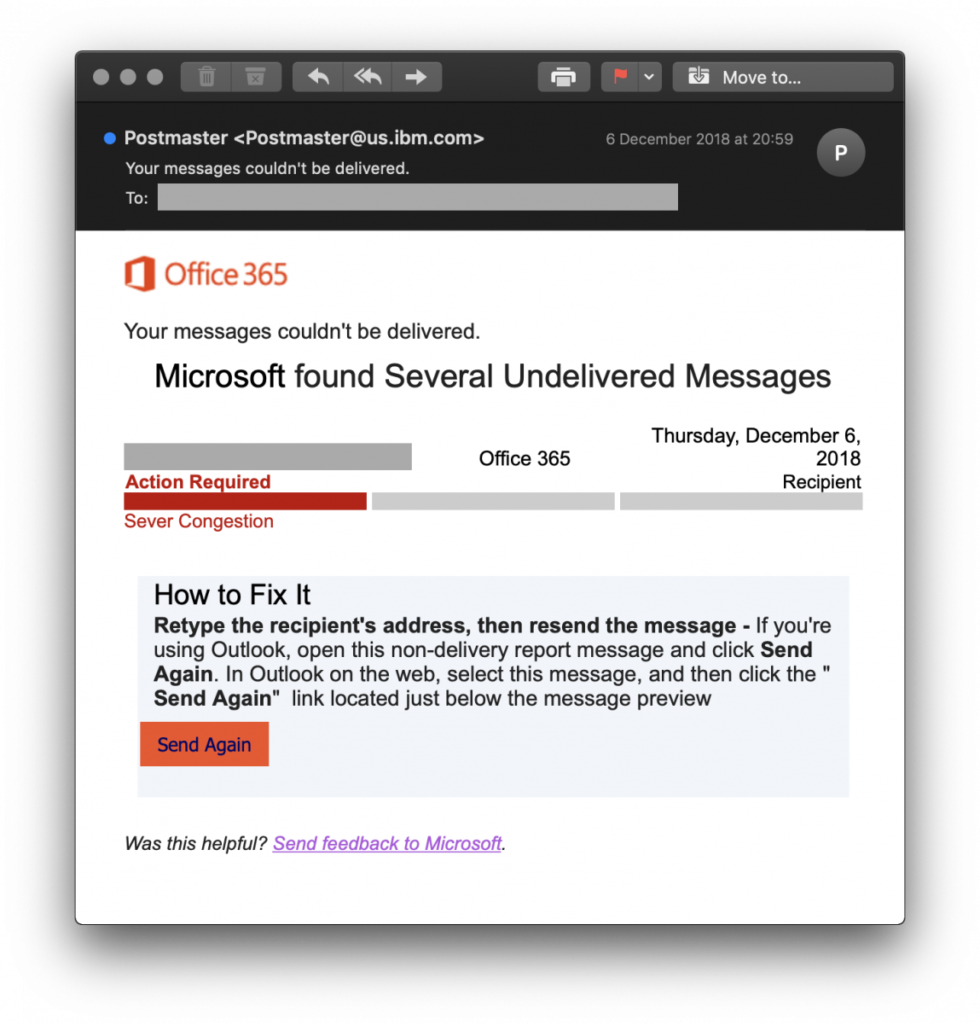
Office 365 Non-Delivery Email Phishing Attack
13th December 2018 | Platform: Office 365| Reported Here
A phishing campaign has been discovered that pretends to be a non-delivery notifications from Office 365 that leads you to a page attempting to steal your login credentails.
This new campaign was discovered by ISC Handler Xavier Mertens and states that “Microsoft found Several Undelivered Messages”. It then prompts you to click on the “Send Again” link in order to try sending the emails again. An example of this phishing email can be seen below.
Quora Gets Hacked – 100 Million Users Data Stolen
4th December 2018 | Website: Quora | Reported Here
The World’s most popular question-and-answer website Quora has suffered a massive data breach with unknown hackers gaining unauthorized access to potentially sensitive personal information of about 100 million of its users.
Quora announced the incident late Monday after its team last Friday discovered that an unidentified malicious third-party managed to gain unauthorized access to one of its systems and stole data on approximately 100 million users—that’s almost half of its entire user base.
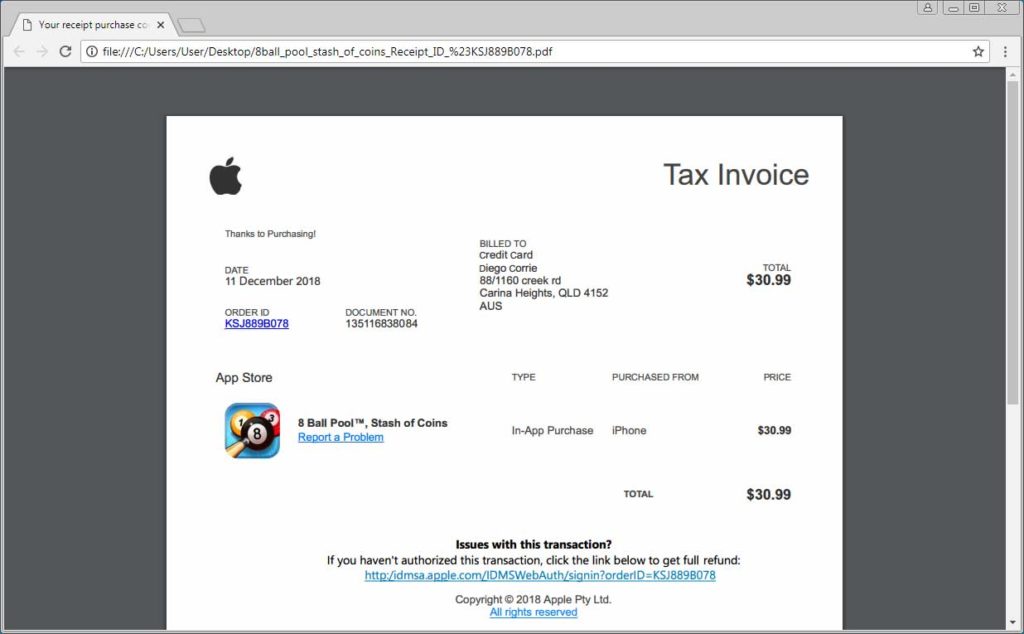
Apple ID Phishing Attack
20th October 2018 | Site: Apple | Reported Here
A widespread and sneaky phishing campaign is underway that pretends to be a purchase confirmation from the Apple App store. These emails contain a PDF attachment that pretends to be a receipt for an app that was purchased by your account for $30 USD and tells you to click a link if the transaction was unauthorized. Once a user clicks the link, down the rabbit hole they go.
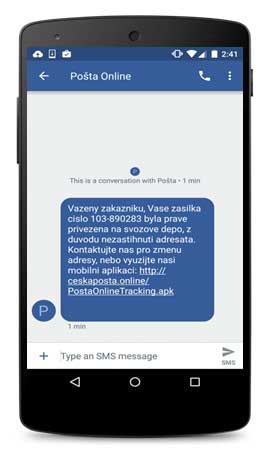
Czech Republic SMiShing Attack
26th January 2017 | Location: Czech | Reported Here
Reports stated that attackers sent smishing text alerts and the SMS sent seemed to be from the Postal Service of the Czech Republic.
Recipients were lead to click on a link which opened up a website designed to look like the official site of the Czech Postal Service which eventually led victims to download malware in the form of an app which contained a Trojan Horse virus.
Sophisticated social engineering tactics which are the hallmark of phishing were employed by the attackers in convincing them to download an app from a non-trusted site.
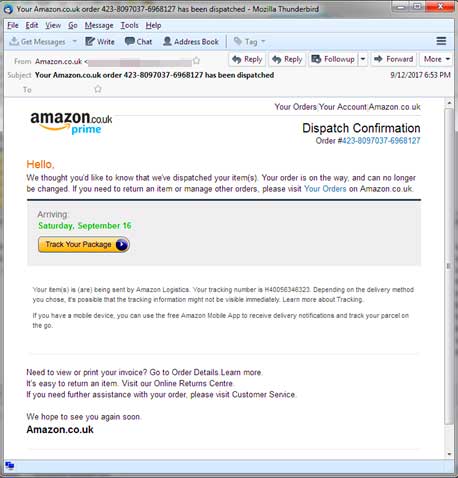
Amazon Locky Ransomware Attack
25th May 2017 | Site: Amazon | Reported Here
Comodo Threat Research Labs states that this massive phishing attack began on May 17, 2016, when cybercriminals sent around a hundred million spam messages to customers around the world. The attack lasted for 12 hours and succeeded in causing tremendous damage to the company’s reputation and the finances of several of its customers.
Phishers sent emails to customers of Amazon with a subject line “Your Amazon.com Order Has Dispatched (#code)” with the sender address as “auto-shipping@amazon.com”.
These emails had a word document attached to them which contained image macros. As customers enabled image macros by clicking on the document, a type of virus called ransomware made its way into their computer systems and encrypted all their files. It then threatened the victims with deletion of their files unless the ransom was paid.
The Walter Stephan Case
25th May 2016 | Company: FACC | Reported Here
Cybercriminals faked the email of the CEO of FACC, Walter Stephan and ordered the employees of his company to hand over vast sums of money to a shady bank account by telling them that it was part of a fictional acquisition project. The attack caused losses to the tune or 47 million dollars to the company. Mr Walter Stephan was then found to be guilty of not carrying out his duties by the supervisory board of the company and had to lose his job.
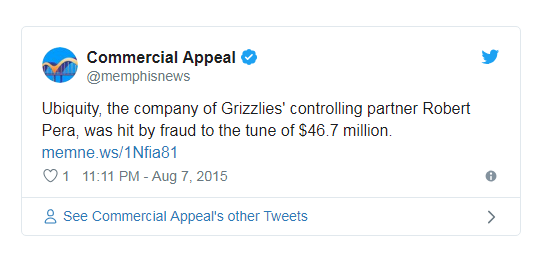
Ubiquiti Networks CEO Fraud
7th August 2015 | Company: Ubiquiti | Reported Here
Ubiquiti is a well-known American technology company and was the unfortunate victim of phishing attacks in June 2015. The attackers were well-prepared and forwarded fraudulent emails requesting wire transfers to the employees of the company.
The unsuspecting employees went on to approve these transactions leading to huge losses of around 40 million dollars for the firm. The firm ended up being able to recover a measly $8.1 million, but the rest of the money ended up in the attacker’s hands.
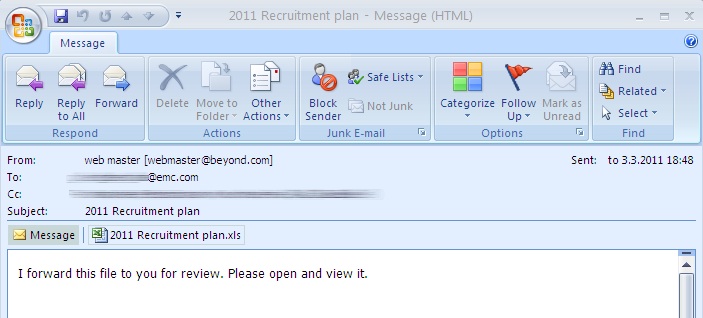
The RSA Attack
26th August 2011 | Company: RSA | Reported Here
The most significant cybercrime case of 2011 was the hacking of the leading security firm RSA by attackers who managed to break into its decidedly secure networks.
The firm sells security solutions to over 40 million businesses and is considered to be one of the world’s leading computer-security companies.
This makes the fact that its employees fell victim to an email phishing attack titled “2011 Recruitment Plan” all the more ironic. It shows us that we can never be too careful when it comes to cybersecurity and even the very best can fall victim to it if not adequately prepared. The Phishing email led employees to download malware via Adobe Flash, which used FTP to transfer several secured RAR files from RSA’s dedicated server to an external host. These files were then removed from the external host, and no traces were left.
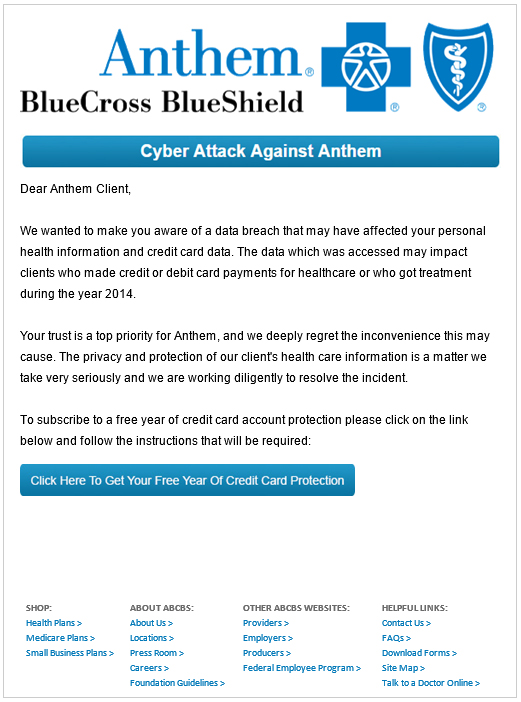
Anthem Server’s Attack
9th February 2015 | Company: Anthem | Reported Here
At around the same time, Ubiquiti was compromised by attackers, and the most massive healthcare breach ever recorded occurred when servers of Anthem was attacked by hackers who succeeded in tricking five employees of the company into opening a phishing mail. This action caused them to download a keystroke-logging malware which in turn led to more than 80 million medical records and files belonging to the Blue Cross and Blue Shield Authority being seized.
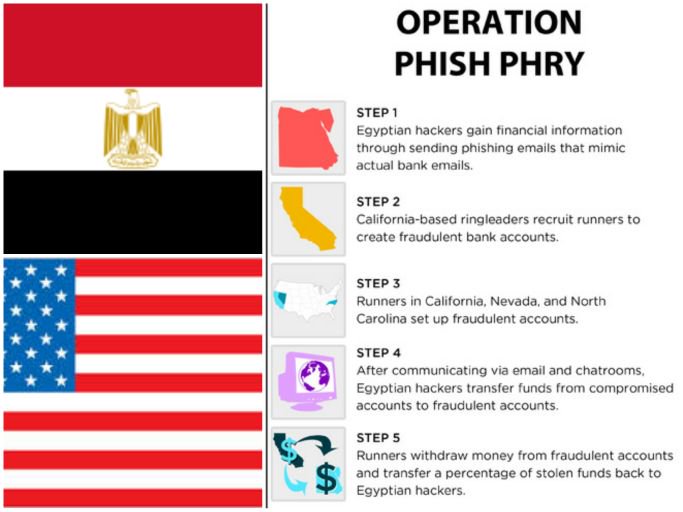
Operation Phish Phry
10th July 2009 | Operation : Phish Phry | Reported Here
Aside from the funny name, Operation Phish Phry was a serious cybercrime investigation which was conducted as a joint operation between the American FBI and Egyptian authorities. The case is historically significant as having had the largest number of defendants on record in the world of cybercrime.
These attackers had illicitly stolen nearly USD 1.5 Million from thousands of victims and transferred their ill-gotten gains to various phoney accounts around the world. These criminals were part of one of the world’s largest nexus of organized crime online dedicated solely to email phishing attacks.