The automobile industry is the new favorite among cyberattackers!
A recent report by Upstream Security reveals that threat attacks on the automobile industry have spiked by a whopping 50%. This sudden surge took place in Q1 2025, and now, neither vehicles nor their manufacturers are safe from cyberattacks.
While 2024 witnessed a total of 409 incidents throughout the year, as many as 148 attacks have already occurred in Q1 2025. The Vice President of Cyber Services at Upstream said that, apart from these 148 incidents, there are many more attacks and activities that would never come to light.
What’s more concerning is the fact that out of these 148 cyberattacks, a staggering 45% were carried out by ransomware gangs. These cybercrooks leverage infostealers to gain access to user credentials, and later sell this data to threat actors who can further weaponize it. These credentials can be misused to impersonate OEM employees as well as car dealers. Through impersonation, they can then gain access to other sensitive details, such as vehicle identification numbers, customer addresses, and vehicle locations.
Such ransomware attacks can cause huge repercussions. For example, a ransomware gang attacked the systems of SaaS provider CDK Global. This company was offering software systems to US car dealers. Due to the cyberattack, operations were disrupted for as long as three weeks. This resulted in a massive loss of $1.02 billion as the threat attack impacted the sales of 56,200 new vehicles.
Autonomous Vehicles, or AVs, and software-defined cars are prime targets for cyberattackers. Even the US government is suspicious of autonomous vehicles and software-oriented vehicles, given the potential for their misuse by nation-state-sponsored threat actors.
Experts believe that the greater the degree of convenience for riders, the higher the degree of risk. Internet connectivity is one of the major reasons why attackers are targeting the automobile industry.
Out of the 148 threat attacks on vehicles this year, 63% fall straightforwardly under the category of privacy data breach. The other 53% comes under the business disruption category. Ransomware groups, such as Lynx, SafePay, and Qilin, are behind some of these major cyberattacks. Experts took no time to underscore a pattern: that cyberattackers are increasingly considering the automobile industry as something vulnerable, easy to target, and also full of possibilities.
Recent threat attack incidents
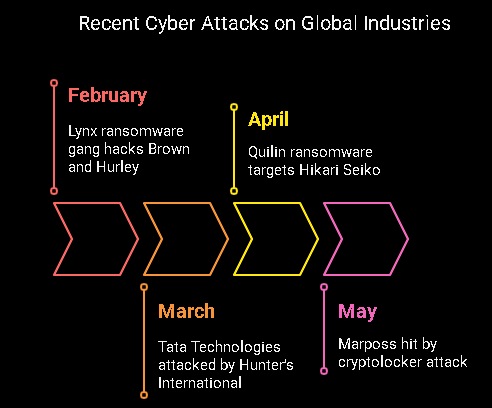
India-based automotive and aerospace service provider, Tata Technologies, was attacked by Hunter’s International, a ransomware gang. It gained access to 1.4TB worth of company data and published over 730,160 files on the company’s website. The IT operations came to a standstill for weeks.
Something similar took place in Japan. The Quilin ransomware gang gained access to 500 GB of company data, including engineering blueprints, supplier agreements, and other sensitive information. The manufacturer, Hikari Seiko, is responsible for producing components of critical importance, such as shafts, gears, and custom-machined parts for some of the biggest OEMs around the world.
It is due to their agility and preparedness that the Japanese manufacturer was able to quickly isolate the infected servers. Also, they were able to restore operations using backups.
In February, the Lynx ransomware gang claimed responsibility for hacking into the systems of the Australian truck dealership company, Brown and Hurley. It managed to steal sensitive data worth 170 GB. This data included employee details, HR records, financial data, business contracts, and customer information. As evidence, Lynx published some parts of the data on the dark web. The Australian truck dealership company has been tight-lipped about any kind of ransom demand and negotiation strategies.
Marposs, an Italian-based high-precision measurement solutions provider, was targeted by unidentified threat actors. The attack led to an abrupt halt in logistics as well as administrative functions. Marposs operates across 34 different nations and has a global team of around 3500 employees. It was a cryptolocker-type attack that encrypted the data and then demanded a ransom for its release.
The attack on Marposs affected multiple stakeholders, including biomedical manufacturers, aerospace manufacturers, and consumer electronics manufacturers, among others. Marposs contacted the postal police as well as the National Cyber Security Agency. Quite unexpectedly, Marposs has also maintained a transparent communication with suppliers and customers. They have been consistent with all the stakeholders about the latest updates and recovery operations.
Final thoughts
According to the recent Upstream report, the number of cybercriminals involved in automotive cyberattacks has increased significantly, jumping from 300 to 1,100.
The rising number of cyber threat incidents targeting the vehicle industry must not be overlooked under any circumstances. In the coming months, it is essential for the industry to adopt a proactive and well-prepared approach to tackle potential cyberattacks. Experts emphasize that automobile manufacturers need to strengthen their security frameworks, with a particular focus on phishing protection.
Developing a robust system that not only defends against cyber threats but also anticipates potential risks and implements preventive measures is more critical than ever.