KillSec Ransomware targets Brazilian health tech company!
MedicSolution, a health tech company in Brazil, was targeted by the notorious KillSec ransomware group in September. 8. The threat actors have managed to steal over 34 GB worth of data. They are now threatening the health tech brand to fulfill their ransomware demand, or otherwise they will leak all the data on the dark web. The stolen data consists of over 94,000 files, including unredacted patient images, X-rays, details, and patient records of minors, and so much more.
After a thorough investigation, they realized that the insecure AWS S3 buckets enabled the cybercriminals to creep into the systems of MedicSolution. Experts also feel that the attack must have taken place way back in the months.
Because of this cyberattack, several other Brazilian healthcare centers are also at high risk, such as Clinica Especo Vida, Labclinic, Vita Exame, Laboratorio Alvaro, and Centro Diagnostico Toledo, among others. This is so because MedicSolution is a software provider that offers cloud storage facilities to different healthcare institutions and clinics so that they can carry out everyday operations with utmost ease.
The ransomware attack has directly affected those patients whose personal details and medical records are listed on MedicSolution. Highly sensitive data, such as medical assessments, test results, and past medical history, has all been compromised—thanks to this breach.
Why are supply chain attacks a growing threat?
Cybersecurity experts believe that supply chains are a favorite target among threat actors. This is so because they are a treasure trove of data. The same data can be exploited to attack multiple targets conveniently. Such attacks enable cybercriminals to carry out large-scale data theft, leading to easy, random demands and smooth payment diversions. The connection between health tech providers and suppliers makes them highly suitable options for cybercrooks.
Another reason why cybercrooks prefer supply chain attacks is the higher degree of untraceability. Such attackers can go untraced for a long time after the cyberattack, which helps them make the most out of their threat campaigns.
What’s more concerning is the fact that the impacted patients have not yet been informed about the ransomware attack. Some of the researchers tried to get in touch with some of these patients and realized that the victims are completely unaware of the cyber mishap. Since they are in complete darkness about the incident, they are in no way prepared to safeguard themselves from any potential cyberattack or scam in the future.
The Brazilian health tech company MedicSolution is not the sole target of the KillSec ransomware group. The latter claims that they have wiped out data from other healthcare institutions such as Columbia, the US, and Peru. All these have happened just a few days before the MedicSolution threat attack.
Doctocliq, another healthcare software solutions provider, was targeted by the same ransomware group almost 30 days ago. This health tech company is based in Peru and offers software solutions to over 2500 health care organizations across 20 nations.
The CEO of Resecurity, Gene Yoo, stated that KillSec was earlier a hacktivist collective. But now it has evolved into a cybercriminal group. The same name is used by so many independent threat actors and other cybercriminal groups. They carry out different types of cybercrimes such as ransomware operations, DDoS attacks, and so on.
KillSec has been following a consistent pattern in its threat campaigns, largely centering on the misuse of exposed and vulnerable cloud resources. This tactic is becoming increasingly common across Brazil, where ongoing economic shifts and rapid digitization create a lucrative environment for cybercriminals. Yoo notes that cybercrooks are treating the region as especially profitable, which highlights the urgent need for stronger defenses, including phishing protection, to reduce the impact of such attacks.
The scenario is absolutely the same for the sudden surge of cybercrimes across South and Latin America.
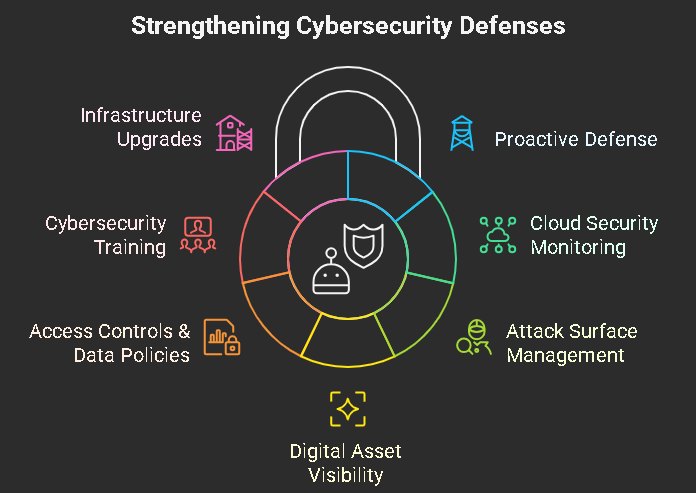
Best practices to mitigate ransomware risks
Adopt proactive defense mechanisms
Experts believe that organizations must adopt strong defense mechanisms to steer clear of such threat risks. From gathering cyber threat intelligence to persistent threat monitoring, organizations must integrate cyber hygiene in their day-to-day operations. Special attention should be given to cyber threats from supply chain vendors and third-party service providers.
Implement cloud security monitoring
Cloud security monitoring helps identify data leaks and misconfigurations early on.
Leverage Attack Surface Management (ASM)
Leveraging Attack Surface Management (ASM) is yet another strategy that helps enterprises detect and remediate any kind of vulnerabilities before a potential threat attack occurs.
Maintain digital asset visibility
Maintaining a constant digital watch over cloud services, servers, applications, and other assets enables the detection of weaknesses in advance, allowing for timely remediation and reducing the risk of intrusions.
Enforce access controls and data policies
Limit access to sensitive health data only to authorized personnel, obtain proper consent before processing personal data, and implement strict data protection policies.
Conduct regular cybersecurity training
Frequent training sessions help staff stay updated on evolving threats and best practices, strengthening the human element of defense.
Upgrade infrastructure and systems
Phasing out outdated infrastructure and continually updating cybersecurity systems helps mitigate risks associated with advanced attack methods.