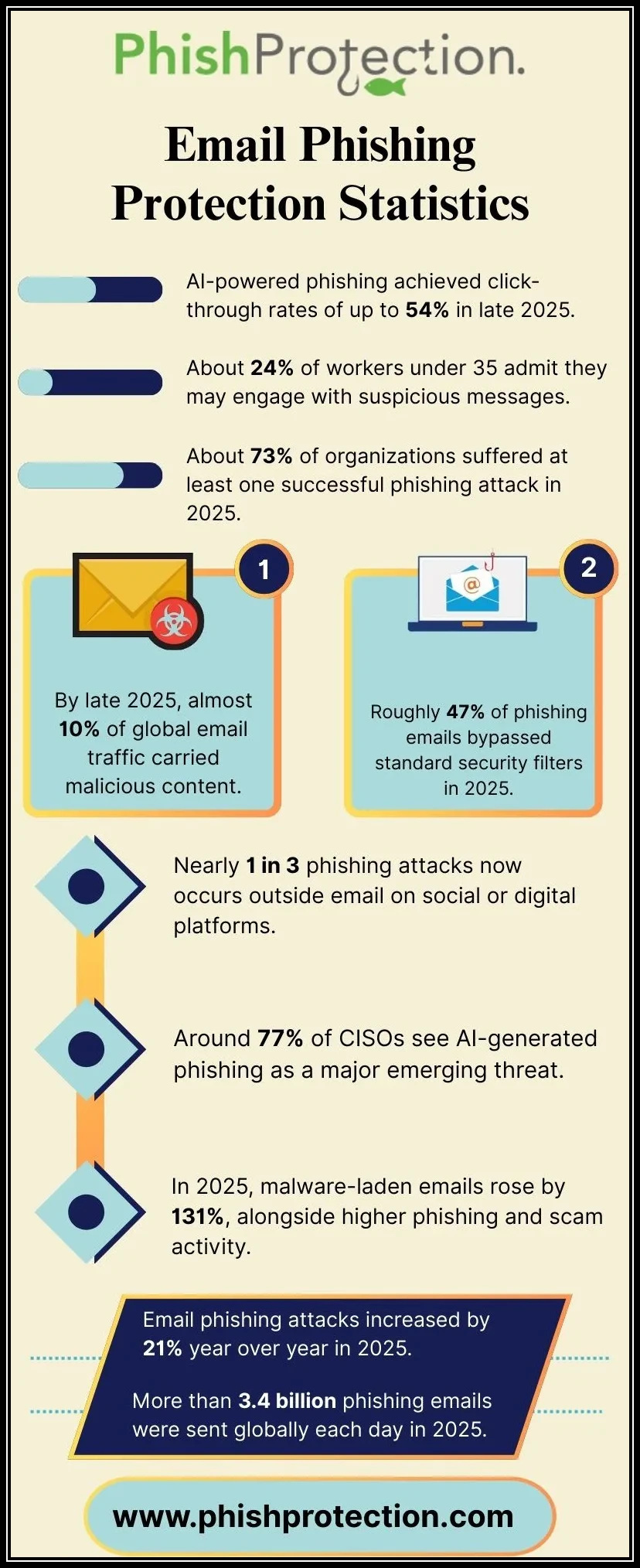
Phishing attacks have evolved into one of the gravest cyber threats affecting businesses and individuals. As enterprises increasingly rely on cloud-based communication platforms like Office 365 and G Suite, the vectors for phishing attacks become more sophisticated and technically advanced. Cybercriminals exploit these channels, targeting business-critical data and leveraging techniques such as email impersonation, business email compromise (BEC), and CEO fraud.
Statistics from leading threat information platforms, including PhishTank and Sophos, report annual increases in phishing attempt incidents, many of which lead to credential theft, malware delivery, and ransomware infiltration. Attackers are no longer resorting to crude scams; instead, they’re deploying advanced threat defense bypasses, harnessing email provider vulnerabilities, and manipulating both on-premise email servers and cloud-based protection systems.
Phishing protection has thus emerged as a critical component of modern email security, ensuring robust safeguards against a broad range of email fraud tactics. Enterprises and small businesses alike need to prioritize email protection, focusing not only on legacy virus protection but also on multi-layer protection that stops spear phishing, ransomware, and malware before they cause harm.
What Are Phishing Protection Services?
Phishing protection services are comprehensive solutions designed to defend organizations from email-based cyberattacks. By incorporating advanced technologies such as anti-phishing software, real-time link checking, and behavioral analysis, these platforms serve as the first line of defense for your email security infrastructure. These services help in blocking phishing attempts, scam prevention, impersonation protection, and offer targeted responses to business email compromise and CEO fraud.
Providers such as PhishProtection, Cyren, and Vade Secure offer both hosted email security and integration with enterprise email security solutions. Their purpose is to identify, quarantine, and neutralize threats before users can interact with a malicious email. The rise of Office 365 vulnerabilities and the popularity of Google’s email services highlight the urgency for Office 365 phishing protection and broader cloud-based email protection overall.
Phishing protection is available through various delivery models, including SMTP service integration, on-premise email server modules, and native plugins for popular platforms like Office 365 and G Suite. The goal across all formats is to provide real-time, layered defenses that mitigate the risks posed by cybercriminals.
Key Features and Benefits of Phishing Protection Solutions
Multi-Layer Protection and Advanced Threat Defense
Today’s anti-phishing software leverages multiple layers of security to counteract varying threat types. This multi-layered approach addresses email impersonation, blocks ransomware, provides malware protection, and is able to detect fake emails in real time. Features such as outbreak protection and virus protection further bolster defenses, stopping threats as soon as they are identified anywhere globally.
Real-Time Protection Capabilities
Best-in-class phishing protection platforms use real-time protection, including real-time link checking and time of click protection. Features like safe URLs and URL classification ensure that when a recipient clicks on a link, the destination is scanned instantaneously for threats. This advanced threat defense mechanism is essential for spear phishing prevention and general phishing prevention efforts.
Adaptability Across Platforms
Enterprise-class email protection isn’t just for desktop clients; leading solutions provide device protection for both mobile (Android device security, iOS device security) and desktop email client protection. This adaptability ensures that users are protected whether they’re accessing business email from a smartphone, tablet, or workstation.
Comprehensive Monitoring and Reporting
Solutions such as those provided by PhishProtection.com and Sophos deliver dashboard statistics, historical stats, and reporting tools that empower IT teams to gain actionable threat information. They support user adoption by making insights accessible, allowing rapid incident response, and demonstrating efficacy to business stakeholders.
Seamless Integration and Managed Services
Phishing protection solutions are designed for seamless integration with most enterprise email security ecosystems, including hosted email security setups and on-premise email servers. MSP partner programs support managed service providers delivering business email security at scale, catering to both small business email security customers and large global enterprises.
Benefits Summary
- Dramatically reduces the risk of email fraud and business email compromise.
- Provides ransomware protection and malware protection.
- Blocks email impersonation and CEO fraud schemes.
- Enforces multiple layers of security through advanced threat defense.
- Enhances enterprise email security for Office 365, G Suite, and more.
- Offers cloud-based protection and compatibility with on-premise infrastructure.
- Drives user adoption with intuitive dashboards and reporting.
- Includes dedicated customer support and an optional free trial/demo request.
Types of Phishing Attacks and How Services Address Them
Classic Phishing and Bulk Campaigns
Mass emails with malicious links or attachments remain prevalent. Solutions with anti-phishing software and virus protection automatically quarantine or block such content using advanced real-time link checking and outbreak protection.
Spear Phishing and Whaling
Targeted attacks such as spear phishing and CEO fraud are particularly damaging, often leading to major business email compromise incidents. Phishing protection services implement spear phishing protection, using AI-driven email analysis, behavioral modeling, and impersonation protection to detect anomalous sender patterns and suspicious content.
Business Email Compromise (BEC) and Email Impersonation
Phishing attacks that involve email impersonation, like pretending to be an executive (“whaling“) or external vendor, are addressed by fake email detection algorithms and sender verification protocols. This level of protection is vital for CEO fraud protection and broader BEC defense.
Ransomware and Malware Delivery
Email remains a primary channel for malware and ransomware propagation. Enterprise-class email protection includes malware protection, sandboxing of attachments, and time-of-click link verification to block ransomware before payload execution.
Zero-Day and Outbreak-Driven Threats
Technically advanced attacks, such as zero-day exploits or rapidly spreading malware, are countered through outbreak protection, real-time threat intelligence sharing (such as with Cyren or PhishTank), and continuous updating of threat databases.
Cloud and Device-Specific Phishing
Targeted phishing attacks seeking to exploit Office 365 vulnerabilities or bypass Google defenses have prompted a new generation of phishing protection tailored for Office 365 security and G Suite integration. Solutions extend their coverage to Android device security and iOS device security to ensure holistic protection.
Assessment: Evaluating Your Organization’s Phishing Risk Level
Before implementing or upgrading a phishing protection solution, assessing your organization’s current risk landscape is critical:
Step 1: Internal Email Security Audit
Conduct a comprehensive analysis of your current email security stack, including legacy virus protection, multi-layer protection, and user training efficacy. Evaluate the configuration of hosted email security, enterprise email security solutions, and integration with existing Office 365 security setups.
Step 2: Review Threat History and Statistics
Leverage reporting tools available in solutions from providers like Vade Secure and PhishProtection.com. Using dashboard statistics, historical stats, and threat information, identify common attack patterns, outcomes of past phishing attempts, and assess resilience against technically advanced attacks.
Step 3: External Vulnerability and Awareness Assessment
If your organization uses Office 365 or G Suite, specifically analyze for Office 365 vulnerabilities and areas lacking in Office 365 phishing protection. Survey employee awareness regarding email impersonation, scam prevention, and spear phishing tactics; review adoption and efficacy of current phishing resources.
Step 4: Test with Simulated Attacks
Leverage available free trials or demo requests for anti-phishing software to conduct simulated phishing attempts. Providers such as DuoCircle and PhishProtection.com offer demo environments to safely assess phishing prevention capabilities and user response.
Step 5: Match Needs to Solutions
Identify whether you require on-premise email server compatibility, cloud-based protection, or hybrid options. Consider the scale required for your environment: enterprise-class email protection for large deployments or small business email security for SMEs. Evaluate MSP partner programs for managed service delivery.
Step 6: Continuous Monitoring and Improvement
Implement solutions that offer actionable reporting tools, ongoing threat information, and adaptive controls. Engage with customer support and partner programs (such as those highlighted on G2.com by reviewers like SJ T., Steve M., and Craig S.), to maintain the highest level of protection as phishing methodologies evolve.
By following these assessment protocols and understanding the spectrum of threats, organizations can build informed, resilient defenses and protect their business from the devastating impact of phishing, ransomware, and business email fraud.
Essential Strategies for Effective Phishing Protection
A comprehensive phishing protection strategy requires a layered approach that incorporates both technological defenses and organizational processes. As phishing attacks grow in sophistication—particularly with technically advanced attacks leveraging AI technology—organizations must be vigilant in their efforts to protect their business-critical data and users from compromise.
Robust Email Security Protocols
Implementing advanced email security solutions is foundational for blocking. Solutions specializing in enterprise-class email protection combine multiple layers of security, including anti-phishing software, malware protection, ransomware protection, and real-time link checking. This is especially vital for environments using Office 365 security or G Suite, as attackers often exploit Office 365 vulnerabilities and weaknesses in email provider security.
Multi-Layer Protection and Outbreak Protection
Effective phishing protection depends on a multi-layer protection model. This includes not only the use of hosted email security and cloud-based protection services but also integration with on-premise email servers for organizations maintaining hybrid environments. Outbreak protection with automated updates to threat information, virus protection, and anti-phishing software ensures defenses remain current as threats evolve.
Impersonation and Business Email Compromise Defense
Mitigating business email compromise and CEO fraud demands targeted impersonation protection. Email impersonation detection, fake email detection, and CEO fraud protection tools safeguard against attackers posing as trusted executives. Such impersonation protection systems can utilize historical stats, URL classification, and machine-learning algorithms to flag anomalies in sender reputation or email content.
User Education and Policy Enforcement
While advanced threat defense solutions are vital, phishing prevention is incomplete without user education. Regular training sessions on email fraud, scam prevention, and updated phishing resources help employees recognize and avoid sophisticated spear phishing attempts and ransomware lures. Enforcing strict email policies further bolsters enterprise email security and small business email security efforts.
Automated Dashboard Statistics and Reporting
Centralized dashboard statistics and advanced reporting tools provide organizations with actionable threat information and user adoption metrics. These insights help administrators refine defense strategies, review historical stats on email fraud and malware protection, and proactively address new vectors exploited by cybercriminals.
Integrating Phishing Protection with Existing Cybersecurity Infrastructure
For maximum effectiveness, phishing protection must seamlessly integrate with established cybersecurity controls and workflows, enhancing broader cyberattack resilience.
API-Based and Proxy Integrations
Phishing protection platforms like PhishProtection.com and Cyren offer flexible API and proxy integrations with both cloud-based protection and on-premise email servers. This ensures compatibility with traditional SMTP service infrastructure while also supporting Microsoft Office 365, G Suite, and major email client protection standards.
Device and Endpoint Security Considerations
Phishing attacks often target endpoints directly. Device protection—including tailored Android device security and iOS device security—adds an extra layer, safeguarding users regardless of access location or device type. This endpoint focus is essential as remote and hybrid work increases attack surface complexity.
Supporting Real-Time and Time-of-Click Protection
Spear phishing protection and ransomware protection solutions with time-of-click protection and real-time link checking capabilities are now industry standards. By evaluating safe URLs at the precise moment a user attempts to access a link, these systems overcome the limitations of traditional static URL blacklists and are effective against technically advanced attacks.
Centralized Management and Partner Ecosystem
Enterprise deployments benefit from centralized management consoles, automated alerting, and integration with security information and event management (SIEM) tools. For managed security service providers, MSP partner programs facilitate large-scale phishing attempt blocking, user adoption, and customer support. Entities like DuoCircle and Vade Secure offer such integrated partner program options.
Top Phishing Protection Service Providers: A Comparative Overview
Organizations seeking enterprise email security should evaluate leading service providers across several criteria, from advanced threat defense capabilities to reporting tools and customer support.
Leading Solutions and Their Unique Value
- PhishProtection.com: Renowned for multi-layer protection, real-time link checking, and integration across Office 365 and legacy SMTP service. Their demo request and free trial options enhance customer experience.
- DuoCircle: Focuses on cloud-based protection, hosted email security, and granular impersonation protection, well-suited for small business email security and MSP partner program adoption.
- Cyren and Vade Secure: Both leverage advanced threat intelligence, outbreak protection, and professional enterprise-class email protection features relevant for global organizations.
- Sophos: Integrates malware protection, spear phishing prevention, and ransomware protection within an accessible dashboard, offering strong device protection and threat information analytics.
Community and Case Study Recognition
Entities such as G2.com showcase peer-reviewed case study highlights from IT leaders like SJ T., Steve M., Florian M., Craig S., Murali K., and Pedro D. User testimonials routinely praise comprehensive reporting tools, effective CEO fraud protection, and real-time response to evolving cyberattacks.
Factors to Consider When Choosing a Phishing Protection Service
Selecting an appropriate anti-phishing software solution demands an objective analysis of several operational and technical factors.
Compatibility and Coverage
- Enterprise email security vs. Small business needs: Consider if the service provides flexibility for different organizational scales, including hosted email security, on-premise email server support, and cloud integrations.
- Email client compatibility: Ensure seamless protection across platforms, including Office 365, G Suite, and other major email provider security services.
Security Feature Set
- Multiple layers of security: Look for solutions offering advanced threat defense, ransomware protection, malware protection, spear phishing prevention and protection, impersonation protection, phishing attempt blocking, URL classification, and time of click protection.
- Device and endpoint protection: Evaluate Android device security and iOS device security options as part of a comprehensive package.
Usability and Insights
- Dashboard statistics and reporting tools: Prioritize offerings with robust dashboard analytics and actionable threat information for continuous improvement and compliance purposes.
- User adoption and support: Strong customer support, rapid user adoption processes, and educational phishing resources are critical. MSP partner programs add value for managed services and resellers.
Licensing, Trials, and Program Involvement
- Free trial and demo request: Test solution effectiveness before full-scale deployment.
- Partner program availability: Especially important for MSSPs and VARs looking to integrate phishing protection into broader cybersecurity portfolios.
Future Trends in Phishing Protection and Emerging Technologies
As cybercriminals continually refine their tactics, future technologies in phishing protection will increasingly leverage automation, intelligence, and user-centric design.
AI and Machine Learning for Phishing Prevention
The adoption of AI-driven analysis is set to revolutionize phishing protection. Pattern recognition, context-aware fake email detection, and anomaly-based alerting are becoming standard for real-time protection against technically advanced attacks. Providers such as Google and PhishTank are advancing real-time link checking and safe urls verification using AI models.
Automated Threat Sharing and Response
Threat intelligence automation and faster threat information dissemination between providers (e.g., Microsoft, Sophos, Cyren) will enable more effective outbreak protection. Integration with SIEMs and orchestration solutions will further empower the automatic defense of business-critical data.
Enhanced Spear Phishing Protection
Emerging spear phishing protection tools will offer deeper integration with enterprise workflows, scrutinizing behavioral patterns and communication metadata to uniquely identify targeted attacks, especially those exploiting Office 365 vulnerabilities.
Expansion of End-to-End Protection Across Devices
Future solutions will enhance protection beyond email, covering unified device protection (including advanced Android and iOS device security) and securing multiple vectors (chat, collaboration tools, cloud storage) to counter increasingly blended cyberattacks.
Emphasis on Usability and Business Integration
Continued focus on simplified UI, improved user adoption, integration with reporting tools, dashboard statistics, and a shift toward self-service demo request and free trial experiences will be hallmarks of future-ready services.
FAQs
What is phishing protection, and why is it important?
Phishing protection includes strategies, technologies, and processes that defend against phishing attacks, which often target email security to steal sensitive credentials or install malware. Effective phishing prevention helps protect your business from email fraud, data loss, and financial loss.
How does advanced threat defense differ from basic email security solutions?
Advanced threat defense uses multi-layer protection, behavioral analysis, and real-time link checking to catch technically advanced attacks like business email compromise and spear phishing, while basic solutions may only block known threats or spam.
Can phishing protection integrate with Office 365 and G Suite?
Yes, top providers such as PhishProtection.com, Vade Secure, and Cyren offer robust Office 365 phishing protection, integrating seamlessly to address Office 365 vulnerabilities and provide enterprise email security for cloud-based email platforms.
What features should I look for in anti-phishing software?
Key features include multiple layers of security, impersonation protection, ransomware protection, time of click protection, real-time threat information, effective device protection (including Android and iOS security), reporting tools, and user training support.
How is spear phishing protection different from general phishing protection?
Spear phishing protection targets highly customized attacks aimed at specific individuals, using sophisticated fake email detection and behavioral analysis, while general phishing protection covers a broader range of attack vectors.
Is phishing protection suitable for small businesses as well as enterprises?
Absolutely. Solutions offering small business email security provide scalable, cost-effective protection, while enterprise-class email protection supports large organizations with advanced threat defense, reporting, and multi-layer protection.
What is real-time link checking, and why is it important?
Real-time link checking analyzes email links at the moment they are clicked, guarding against dynamically changing malicious URLs and ensuring users only access safe URLs, a critical feature for effective email protection.
Key Takeaways
- Multi-layer protection, real-time link checking, and advanced threat defense are essential for robust phishing protection.
- Integrating phishing protection with existing cybersecurity systems ensures comprehensive defense against evolving email-based cyberattacks.
- Leading providers like PhishProtection.com, DuoCircle, and Cyren offer scalable, enterprise-class email protection with strong reporting and impersonation protection.
- AI-driven fake email detection and behavioral analytics represent the future of spear phishing prevention and defense against sophisticated email fraud.
- Scalable solutions support both small business email security and large enterprise requirements, with flexible partner programs and customer support enhancing user adoption.