The threats in the cyber world are looming over businesses of different sizes these days. Technology has facilitated the work of businesses tremendously, but new risks of cyber attacks appear simultaneously to the benefits they enjoy.
Just as we research cyber threats and uncover new security measures to prevent them from happening, hackers find innovative ways to achieve their goals. They even have their ways to uncover vulnerable companies to hack and avoid the ones with fierce security measures in place.
This is why businesses need to keep up with the ever-changing cyber threats consistently. The safety measures that protected your organization just last year might not work today. According to TechJury, 30,000 new pieces of malware are being created every single day.
With this in mind, we’d like to present you with the 4 common cyber threats that you should know about in 2022. We’ll accompany this information with some actionable tips on how to avoid and prevent them.
1. SQL injection attacks
This type of cyber threat has found itself in the top ten list of security risks according to OWASP. In recent years, SQL injection attacks are one of the most common types of cyber attacks, especially on ASP and PHP applications.
The SQL databases contain attractive data to hackers i.e. user account information, login credentials, payment details, etc. To put it simply, an SQL injection is a technique that uncovers security holes in data fields like search bars and contact forms – or even in web pages.
If the company doesn’t protect the input process properly, hackers discover such areas and inject malicious commands that make the database perform unwanted actions.
For hackers, these are cheap and simple attacks, but the consequences for a business can be devastating. If the cyber attack is successful, the criminal will be able to do everything from deleting content from the database to extracting the most sensitive data of customers, and even manipulating transactions.
The worst part is, that attackers can discover these vulnerabilities with minimal effort. They use bots to scan your site and features and once they identify a vulnerability, they simply input malicious commands.
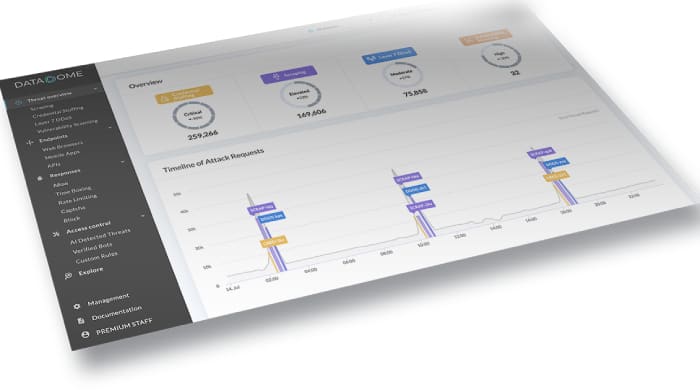
Preventing SQL injections with DataDome
Everyone is vulnerable to this type of attack these days, but do not despair. There is a simple solution to this. Since hackers hardly ever attack databases based on a hunch or manually, they’ll need to go for methods like intensive scraping, Layer 7 DDoS attacks, and credential stuffing.
These attacks have the most aggressive bots, which is where DataDome can do wonders for securing your business. The tool detects SQLi vulnerability bots almost immediately, and will automatically block them before they can do damage.
DataDome is a trending SQL injection prevention solution used by some of the top brands in the world. It deploys in minutes on all web infrastructure and runs on autopilot so you don’t have to do anything.
At the same moment, Data Dome analyzes billions of events using AI and ML. It can determine if a visitor is a bot or a real customer in less than 2 milliseconds, which makes it the perfect tool against this type, or other common types of attacks.
2. Phishing
To this day, phishing remains the top email threat, as well as the most significant cybercrime in the world. In the first two quarters of 2022, there’s been a reported increase of 48% in email attacks, and no less than 68.5% of these include phishing links.
Criminals are becoming much more creative with this, too. Email remains the most used communication method in the business world, which makes it the perfect place to conduct their fraudulent activities.
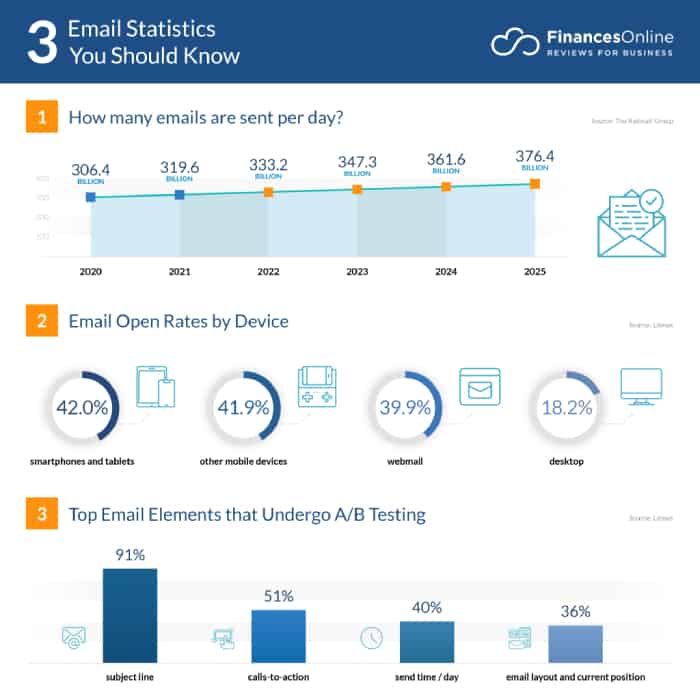
Every day, 333.2 billion emails are sent, and the numbers are estimated to grow significantly in the years that follow. This means that email will remain a highly used place for cybercriminals, and phishing attacks won’t disappear any time soon.
Ways to detect and prevent phishing attacks
Fortunately, the majority of phishing attacks are easy to recognize. As a matter of fact, most will be flagged by your email provider and put in the spam or junk folders.
Even so, spammers often update their phishing tactics, which means that some messages will slip the email filters.
Let us give you some examples of what most phishing emails include:
- Fake invoice for something you haven’t bought
- A claim that there’s been suspicious activity for some of your tools or profiles
- Links for making payments or strange requests by companies that do not exist
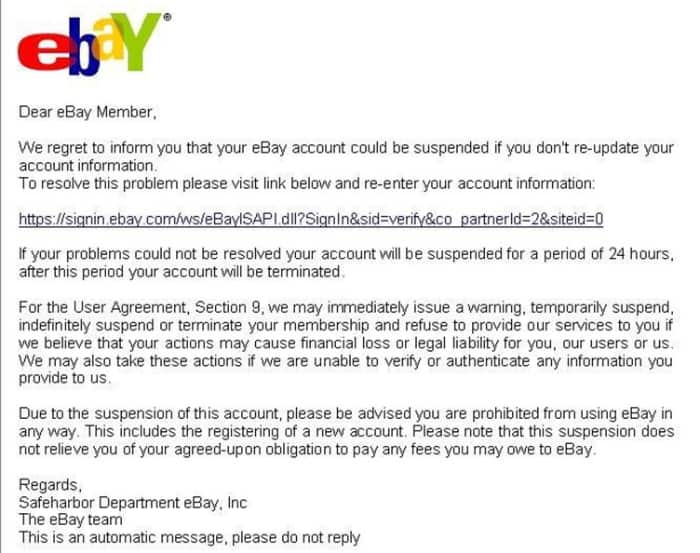
- A claim that there’s been a problem with your payment details or your account (check the example below)
3. RDP attacks
Just as phishing and SQL injection attacks, RDP attacks are also on the rise this year. RDP is an integral piece of the operating system of a computer that allows users to connect to devices from remote locations.
The reason why these attacks are so frequent these days is because of the pandemic. As you know, the pandemic has prompted a big increase in remote work. Many people started working from home, so they needed to access the computers in the office.
This trend continues even today. Remote work is one of the most demanded benefits across the world at this point. Research shows that 99% of employees would like to work remotely at least partially and at least at some point in their career.
The awareness of the perks of remote work has increased, so people are choosing to work remotely all over the world. This means that many are accessing a variety of devices by using RDP, which is why the number of such attacks is on the rise, too.
How do RDP attacks work, really?
To log into a computer using this technology, you need to type in the internet address of your device, as well as your username and password. IP addresses can easily be found, which makes computers that use this highly vulnerable to RDP attacks.
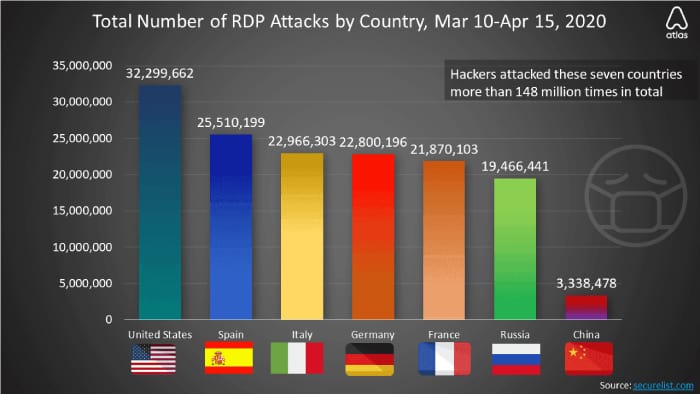
Let’s take a look at the numbers for RDP attacks in 2020.
Since remote work doesn’t seem to diminish in popularity, we can only expect these numbers to grow. Once the hacker gets access to your device, they can do everything from deploying malware and ransomware to accessing different endpoints connected to the same network. Just imagine that – the criminal getting access to all the devices in the office!
Hackers are known to deploy spyware to keep track of what your business is doing, or even uninstall phishing protection solutions like antiviruses to make your business even more vulnerable to other cyber threats. They can delete system backups, steal sensitive information, and basically destroy your company altogether.
How to minimize your vulnerability to an RDP attack
There’s no sure way to protect your devices from such attacks, but there are some ways to reduce the risks. For starters, you might want to consider not using RDP protocols to access your devices. If this can be avoided, that’s definitely a way to avoid an RDP attack.
You could also limit user access to minimize the number of people that have access to your devices, or limit the access to specific IP addresses, which will automatically block the unknown ones.
On top of this, you can create stronger passwords and use rate limiting to set the number of permitted login attempts. When the bots of criminals attempt several times to guess your password, the rate-limiting feature will shut them out.
Other methods include using VPN, network level authentication, and multi-authentication for accessing your device.
4. Man-in-the-middle attacks
The fourth in our list of most common cyber threats in 2022 is the MITM attack. The increase in such attacks is also mostly a result of the pandemic. With many people still working remotely, the risk is increased.
Why is this the case?
Remote workers today don’t work exclusively in their homes. They go to coworking spaces, log in to Wi-Fi in the hotels they stay in during a vacation, relax in a coffee shop or restaurant, etc. Many will use unsecured wifi connections to do their work, which makes them vulnerable to MITM attacks.
These types of attacks allow criminals to view the screen of the victim, intercept emails that contain sensitive information, and even get control over the device.
How to avoid MITM attacks
This attack resembles peeking, and the best way to remove the risk is to educate your team that they should avoid using public networks when working. You can also employ VPNs to ensure secure connections, as well as consider extra encryption for emails like SSL/TLS or PGP/GPG.
Your business’ safety is in your hands
Thinking that your business is at lesser risk than others because of its size or popularity is a grave mistake. Businesses without proper security measures in place are at the highest risk of cyber attacks. If you haven’t implemented such measures, you better start today to prevent falling victim to the most common threats.
Author bio:
Nadica Metuleva is a freelance writer who’s passionate about creating quality, original content. She holds a Master’s degree in English teaching and a Bachelor’s degree in translation. With 8 years of experience in the freelance writing industry, Nadica has become proficient in creating content that captivates the audience, drives growth, and educates. You can find her on LinkedIn.