Here are the latest headlines from this past week to keep you updated on the latest techniques and tactics threat actors adopt to lure individuals and organizations into cyberattacks.
Over 5 Million Downloads, But The Parental Control App Is Vulnerable To Attacks
The ‘Parental Control – Kids Place’ Kiddowares Android app contains multiple vulnerabilities that attackers can use to steal user credentials, upload arbitrary files on protected devices, and allow children to bypass controls without their parents noticing, say researchers at SEC Consult.
The Kids Place, a parental control suite, has over 5 million downloads on Google Play. It offers parents to monitor their children through geolocation capabilities, enable screen time management, remote device access, harmful content blocking, and more.
Researchers discovered that the Kids Place app’s older versions than 3.8.49 were vulnerable to the following security flaws:
- User registration and logins returned the unsalted MD5 hash, which hackers can easily intercept and decrypt.
- Attackers can manipulate the child device’s customizable name to trigger an XSS payload.
- Cybercriminals can exploit the app’s dashboard to upload malicious files (it was initially intended to send up to 10 MB files to their children’s devices).
- Since there is no antivirus scan for the uploaded files, the hackers’ job is easier.
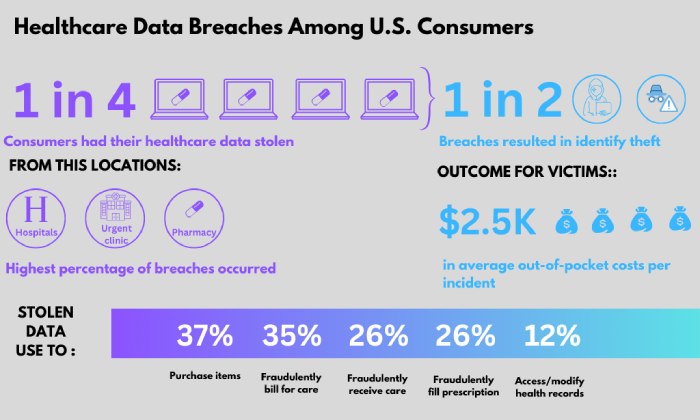
PharMerica Reports Data Breach Affecting 5.8 Million Individuals
National pharmacy network PharMerica recently started notifications to over 5.8 million individuals to disclose that a data breach had taken place in March.
Owned by BrightSpring Health, a home and community health services provider, PharMerica operates close to 2,500 facilities across the US, offering more than 3,100 healthcare and pharmacy programs. On Friday, PharMerica notified the Maine Attorney General’s Office regarding a data breach that may have accessed the personal information of over 5.8 million individuals in March.
According to the company, the data breach occurred between March 12 and 13. Personal information that might have been compromised during the incident includes names, birth dates, Social Security numbers, addresses, health insurance, and medication information.
In some cases, the compromised information was linked to deceased individuals, and PharMerica encouraged surviving spouses to contact national credit reporting agencies. PharMerica’s letter did not provide details regarding the type of cyberattack it suffered, but it appears the Money Message ransomware group was behind the incident.
La Malle Postale, A French Transportation Company, Leaks Personal Data And Private Chats Of Their Clients
The Cybernews research team recently discovered that La Malle Postale’s system was leaking data that contained its clients’ personal data. The exposed information included names, emails, private communication through text messages, phone numbers, passwords, and employees’ credentials.
Founded in 2009, La Malle Postale offers luggage and passenger transportation services on popular hiking routes, including the most visited Santiago de Compostela pilgrimage trail. The clients have well-reviewed their services, giving an overall four-star rating on TripAdvisor.
The company left their employee passwords vulnerable to cracking by encoding them using the Base64 algorithm. Since hackers can reverse and decode the encoded data back to its original format, encoding is not the most secure way to store passwords.
Leaking employee credentials can put the company at risk of targeted cyberattacks where threat actors will exploit the data, gain access to the company’s network, and steal sensitive information.
Toyota Exposed Car Location Data Of 2 Million Customers For Ten Years
Toyota Motor Corporation said that a data breach on its cloud environment had exposed the car-location data of 2 million customers for ten years, from November 6, 2013, to April 17, 2023.
A security notice published in Toyota’s Japanese newsroom says the data breach resulted from a database misconfiguration that allowed hackers to access its contents without a password.
“After the discovery, we implemented phishing protection measures to block outside access, but we are continuing our investigations of all cloud environments managed by TC. We greatly apologize for causing inconvenience to our customers and related parties.” reads the notice.
This incident exposed customers’ information who used Toyota’s T-Connect G-Link, G-BOOK, or G-Link Lite services from January 2, 2012, to April 17, 2023.
Google Announces Latest Privacy, Security, and Safety Features Across Its Services
Google recently unveiled many new privacy, security, and safety features at Google I/O, its annual developer conference. The tech giant’s latest initiatives aim to protect its users from cyber threats, including malicious websites and phishing attacks while providing better transparency and control over their personal data.
The newly introduced features include-
- Improved data control and transparency
- Gmail Dark Web Scan Report
- Effortlessly Delete Maps Search History
- AI-Powered Safe Browsing
- Content Safety API Expansion
- About this Image
- Spam View in Google Drive
Twitter Finally Plans To Roll Out Encrypted Direct Messages — Only For Verified Users
Twitter is officially rolling out encrypted direct messages (DMs) more than five months after its CEO, Elon Musk, confirmed plans for the latest feature in November 2022.
“Phase 1” of the planned initiative will look like separate conversations near the existing direct messages in users’ inboxes. Encrypted chats will carry a lock icon to differentiate them visually.
Furthermore, the opt-in feature will be limited to verified users or affiliates of a verified organization. Also, to use the feature, both the sender and recipient must be running the latest version of the Twitter app.
While Twitter did not disclose precisely how it will secure the conversations, it said it employs ” strong cryptographic schemes” to encrypt the users’ messages, reactions, and links.

![Vulnerable Parental Control: 5M+ Downloads, Data Breach 5.8 Million Affected,French Transport Leaks – Cybersecurity News [12 June 2023]](https://www.phishprotection.com/wp-content/uploads/2023/06/anti-phishing-software.jpg)