Life & Times of Kevin Mitnick – The World’s Most Wanted Hacker
Life Snapshot
Kevin Mitnick, “The World’s Most Famous Hacker,” was born in Los Angeles, CA in 1963. In the late 80s and early 90s, Mitnick used social engineering to hack the computer systems of various companies.
According to his Wikipedia page, in 1999, Mitnick pleaded guilty to four counts of wire fraud, two counts of computer fraud and one count of illegally intercepting a wire communication. He would go on to serve five years in prison followed by three years of supervised release during which time he was forbidden to use a computer.
Today Mitnick runs Mitnick Security Consulting LLC, a computer security consultancy and is part owner of KnowBe4, a provider of security awareness training, that also provides anti phishing software like PhishProtection.com. He does computer security consulting and penetration testing for Fortune 500 companies as well as the FBI.
“At the end of the day, my goal was to be the best hacker.” – Kevin Mitnick
Kevin’s Books
|
|
|
|
|
Kevin Recommends
Kevin is a big advocate of personal privacy online. He advocates the following measures to maintain online privacy:
Encrypted emails
For maximum privacy, emails should be encrypted end-to-end using a publicly available encryption algorithm. Using a public algorithm ensures it has been “vetted for weaknesses.” He believes that if an app or service doesn’t use end-to-end encryption, you should choose another one.
In support of encrypted emails, private key management is very important. A private key should never be shared with anybody. Also, protecting metadata is required to become truly invisible in the digital world.
“The hacker mindset doesn’t actually see what happens on the other side, to the victim.” – Kevin Mitnick
Defend your anonymity
In order to remain anonymous online, several basic steps are required:
- Hide your true IP address. One way to do that is to use a service known as an anonymous remailer, which will mask your email’s IP address for you. Another tactic is to use the onion router for browsing the web. Tor works by changing the path between you and your target website constantly.
- Obscure your hardware and software. If you decide to use Tor, you should not run it in the same physical device that you use for general browsing. In other words, have a laptop for browsing the web and a separate device for Tor.
- Create a new account. You will need to create a new, anonymous account for using Tor so that the IP address setting up the account is not associated with your real identity in any way.
- Isolate activities. You should never perform any internet searches while logged in to an anonymous email account. You might inadvertently search for something that is related to your true identity.
“I saw myself as an electronic joy rider.” – Kevin Mitnick
How to Troll the FBI According to Kevin
At the time of his arrest in 1995, Kevin Mitnick was the most wanted cyber criminal in the United States. The arrest marked the end of an intense two-and-a-half-year electronic manhunt, a game of cat and mouse that Mitnick likens to a video game.
“I was a little bit insane,” Mitnick admits. “Why I did this psychologically is I loved putting myself in dangerous situations and then trying to work my way out of them.”
“A hacker doesn’t deliberately destroy data or profit from his activities.” – Kevin Mitnick
Kevin Mitnick Quiz
Results
#1. What’s the only on-screen credit Kevin Mitnick has in which he doesn’t play himself?
#2. How many corporations is Mitnick credited for having hacked into?
#3. What’s the name of the group of pranksters he joined up with in high school?
“I was addicted to hacking, more for the intellectual challenge, the curiosity, the seduction of adventure; not for stealing, or causing damage or writing computer viruses.” – Kevin Mitnick
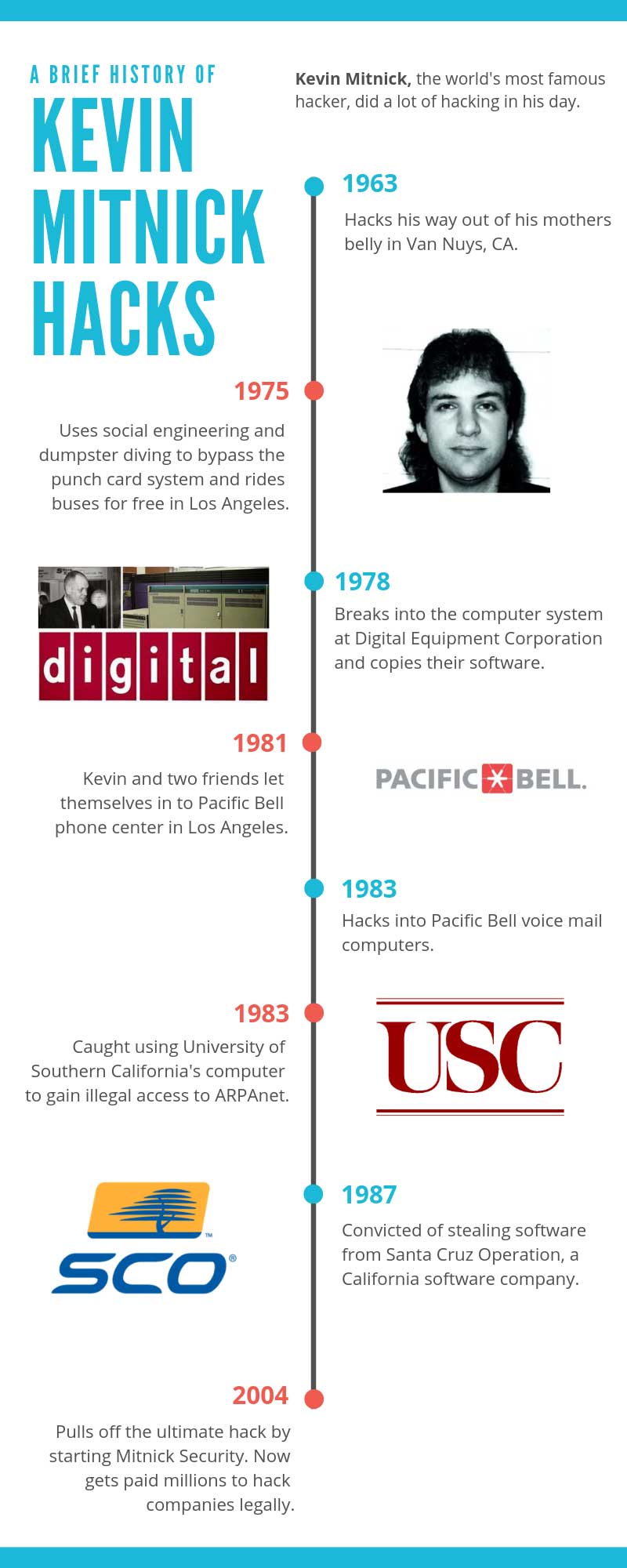
Kevin’s Hacks
Kevin Mitnick Wanted
“You can never protect yourself 100%. What you do is protect yourself as much as possible and mitigate risk to an acceptable degree. You can never remove all risk.” – Kevin Mitnick
Takedown
The book “Takedown” details the pursuit of Kevin Mitnick that led to his capture. It was written Tsutomu Shimomura (Stanford) with contributions by John Markoff. Shimomura who led the mission and has written the book from his experiences. Of course, there are many who say that the events in the book are biased and innacurate and Shimomura has spiced up many of the events and changed the perspectives.
Kevin Mitnick Busted
One of the worlds Top-Best most famous number one hacker Kevin Mitnick shares his FBI bust story on an interviewed
“I was hooked in before hacking was even illegal.” – Kevin Mitnick
Kevin Gets Released
X-Hacker
“The best thing to do is always keep randomly generated passwords everywhere and use a password tool to manage it, and then you don’t have to remember those passwords at all, just the master password that unlocks the database.” – Kevin Mitnick
Kevin on 60 Minutes
60 Minutes segment on Kevin Mitnick.
Kevin Mitnick Live at CeBIT
He is the most famous hacker of the world – and at CeBIT Global Conferences 2015 he performs a hack live on center stage: Kevin Mitnick.
“My argument is not that I shouldn’t have been punished, but that the punishment didn’t fit the crime.” – Kevin Mitnick
Ghost in the Cloud, Strictly Mobile
Once one of the FBI’s Most Wanted because he hacked into 40 major corporations just for the challenge, Kevin is now a trusted security consultant to the Fortune 500 and governments worldwide.
Kevin and The Global Ghost Team™ now maintain a 100 percent successful track record of being able to penetrate the security of any system they are paid to hack into using a combination of technical exploits and social engineering. As CEO and chief “white hat” hacker at one of the most advanced boutique security firms in the world, Kevin mentors leaders, executives, and staff on both the theory and practice of social engineering,
“Hacking was the only entertainment that would occupy my mind – like a huge video game, but with real consequences. I could have evaded the FBI a lot longer if I had been able to control my passion for hacking.” – Kevin Mitnick
Kevin Talks at Google
Kevin Mitnick visits Google’s NYC office to discuss his book “Ghost in the Wires: My Adventures as the World’s Most Wanted Hacker” with Eran Feigenbaum, Google’s Director of Security for Google Apps. This event took place on August 17, 2011, as part of the Authors@Google series.
Kevin Mitnick was the most elusive computer break-in artist in history. He accessed computers and networks at the world’s biggest companies–and however fast the authorities were, Mitnick was faster, sprinting through phone switches, computer systems, and cellular networks.
“As a young boy, I was taught in high school that hacking was cool.” – Kevin Mitnick
Kevin Mitnick Shares the Newest “Shocking” Security Exploits
Outlook Exchange Exploit
In a recent webinar, Kevin demonstrated how a bug in Microsoft Exchange “allowed anyone on an Exchange server to impersonate anyone else on that Exchange server.” In the webinar Kevin simulates gaining access to Jeff Bezos’ (Amazon) account and sends an email from Jeff to the accounting department at KPMG requesting that they change wiring instructions.
Password Hack – No Click or Attachment Necessary
In another webinar, Kevin “shows how hackers can steal a user’s password hash without the user having to click a hyperlink or open an attachment.” This really is the scariest of all phishing scenarios, and perhaps shouldn’t even be thought of as phishing. Afterall, phishing is really duping someone into doing something they don’t want to do. With this new password hack, the victim doesn’t even have to be complicit and they can still get exploited.
WhatsApp Hack
Facebook admitted to a major security breach of its WhatsApp messaging system. The flaw enables hackers to install surveillance spyware in the application itself. It affects both iPhone and Android devices.
In an interview with Kevin, Canadian Broadcasting asked him how something like this could happen. Kevin said, “A lot of these applications are developed by application developers using millions of lines of code and people make mistakes. And what happens is security researchers find these flaws and they’re able to develop exploit code to take advantage of these flaws and do exactly what was done in this case.”
He went on to say, “It’s pretty scary because all an adversary would have to do is ring your phone over WhatsApp and then they would have the ability to install malware. So, it’s a huge wakeup call that these threats actually exist.”
The scariest thing of all is that none of these exploits require interaction from the user.